Introduction
In today’s digital age, information security has become incredibly important. Whether you’re making an online purchase, sending a private message, or securing government communications, the need to protect this information has led to the development of fields like cryptography and cryptology. While these terms are often used interchangeably, they refer to different areas of study with unique purposes, tools, and applications.
In this article, we’ll explore cryptography vs cryptology how they differ, and why both are crucial in securing data. By the end, you’ll understand how they work together to protect information in today’s
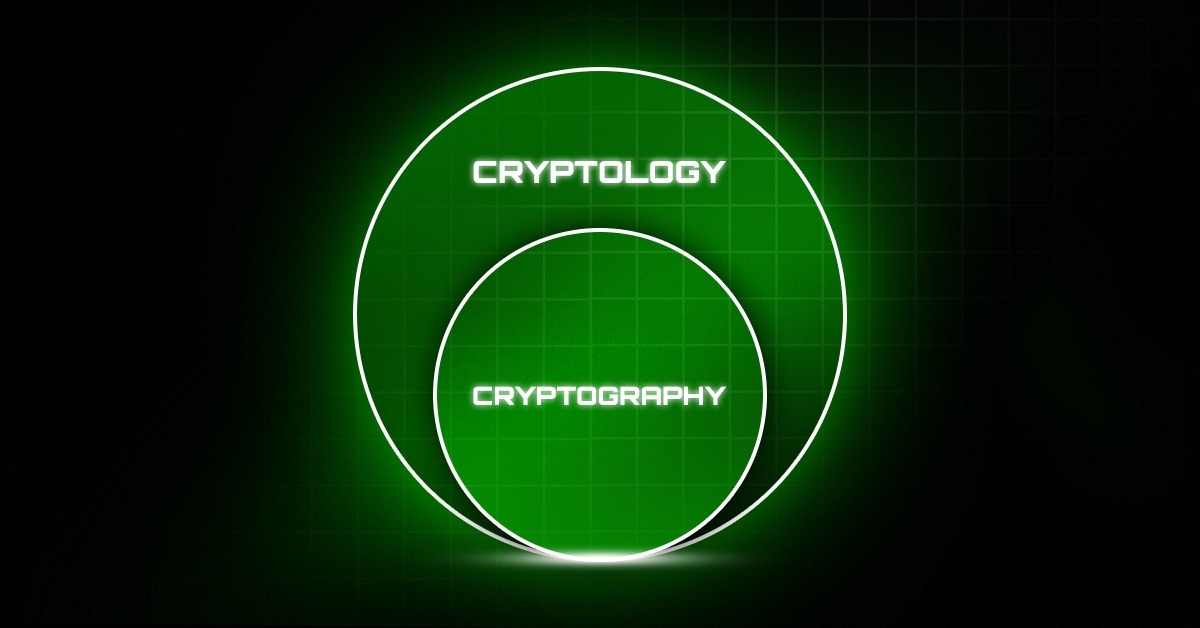
Table of Contents
What is Cryptography?
Cryptography is the art and science of keeping communication secure. It involves techniques that turn readable information into unreadable formats, ensuring that only authorized people can access it. The main focus of cryptography is to protect data, ensuring its confidentiality, integrity, authenticity, and non-repudiation.
Key Concepts in Cryptography
- Encryption and Decryption:
- Encryption is the process of converting readable information (plaintext) into a scrambled format (ciphertext) using a specific method or algorithm.
- Decryption is the reverse process, where the scrambled information (ciphertext) is turned back into readable information (plaintext).
- Algorithms and Keys:
- Cryptographic methods rely on algorithms and keys. A key is information that determines how the encryption and decryption processes work.
- There are two main types of cryptography:
- Symmetric cryptography: The same key is used for both encryption and decryption.
- Asymmetric cryptography: Different keys are used for encryption and decryption, known as the public key and private key.
- Hash Functions:
- A hash function is a method that takes input data and creates a unique fixed-size output. This is commonly used to store passwords securely or ensure the integrity of a file.
Example: AES (Advanced Encryption Standard)
AES is a popular symmetric encryption algorithm used to secure sensitive information. For example, when you make an online purchase, AES might be used to encrypt your payment information, ensuring that only the intended recipient can read it.
Importance of Cryptography
Cryptography is essential for keeping our online activities secure. It is used in everything from protecting your bank details during online shopping to securing classified government information. Without cryptography, it would be easy for attackers to steal sensitive data, making it crucial for the digital age.
What is Cryptology?
Cryptology is a broader field that includes both cryptography (the creation of secure communication systems) and cryptanalysis (the study of breaking these systems). In simple terms, cryptology covers both the methods to protect data and the techniques to analyze or break those methods.
Key Components of Cryptology
- Cryptography:
- As discussed earlier, cryptography is the creation of systems that keep communication secure.
- Cryptanalysis:
- Cryptanalysis focuses on finding weaknesses in cryptographic systems. Cryptanalysts study how to break encryption techniques, sometimes to improve them or, in other cases, to expose their vulnerabilities.
Example: Breaking the Enigma Code
During World War II, Germany used a machine called Enigma to send encrypted military messages. The code created by Enigma was considered unbreakable, but cryptanalysts, led by Alan Turing, were able to break it, giving the Allies a significant advantage during the war.
The Role of Cryptology in Modern Security
Cryptology plays a vital role in improving digital security. While cryptography creates security measures, cryptanalysis ensures that these methods are strong enough to withstand attacks. This balance helps constantly improve the security of digital communications.
Cryptography vs Cryptology: Key Differences
Although closely related, cryptography and cryptology are distinct in their focus and methods.
Aspect | Cryptography | Cryptology |
|---|---|---|
| Definition | The science of creating secure communication systems. | The broader field includes both cryptography and cryptanalysis. |
| Focus | Protecting information using encryption techniques. | Both securing information and analyzing or breaking cryptographic methods. |
| Components | Encryption, decryption, keys, algorithms, hash functions. | Cryptography and cryptanalysis (the study of breaking codes). |
| Goal | Ensure confidentiality, integrity, and authenticity. | Ensure secure communication and analyze vulnerabilities. |
| Real-World Example | AES encryption securing online transactions. | Breaking the Enigma code during World War II. |
| Skills Required | Mathematics, computer science, algorithm development. | Cryptographic knowledge, problem-solving, and mathematical analysis. |
| Primary Users | Security engineers, IT professionals, developers. | Cryptanalysts, researchers, intelligence agencies. |
Real-World Applications of Cryptography
- E-Commerce:
- Cryptography is used to secure online shopping. When you enter your payment information, encryption ensures it is protected from attackers.
- Messaging Apps:
- Applications like WhatsApp use end-to-end encryption, ensuring that only the sender and receiver can read the messages.
- Banking:
- Cryptography protects online banking transactions. Banks use methods like 3-D Secure to authenticate users and protect their sensitive information.
- Government Communications:
- Governments use cryptography to secure classified communications, ensuring that unauthorized parties cannot access sensitive information.
Real-World Applications of Cryptology
- Cybersecurity:
- Cryptanalysts work to find weaknesses in encryption systems used by financial institutions, governments, and businesses. They help improve security by identifying vulnerabilities.
- Blockchain Technology:
- Cryptology plays a key role in securing blockchain systems by ensuring the integrity of transactions and the security of users’ private keys.
- National Intelligence:
- Intelligence agencies use cryptology to secure their communications and to break the codes used by adversaries in warfare and espionage.
Advances in Cryptography and Cryptology
Post-Quantum Cryptography
Quantum computers potentially threaten current cryptographic algorithms because they can solve problems that traditional computers cannot. Post-quantum cryptography aims to develop new encryption methods that are resistant to attacks from quantum computers.
Example: Lattice-based cryptography is one approach being researched to withstand quantum attacks.
Zero-Knowledge Proofs (ZKPs)
Zero-knowledge proofs allow one party to prove they know a value without revealing what that value is. This technique is being applied in blockchain technology to enhance privacy and security.
key areas of progress
1. Post-Quantum Cryptography (PQC)
- What’s the problem? Today’s encryption methods (like RSA) could be cracked by powerful quantum computers in the future.
- What’s new? Researchers are developing new algorithms, such as lattice-based cryptography, that can withstand quantum computing attacks. Efforts are underway to standardize these new methods.
2. Homomorphic Encryption
- What’s the problem? How do we keep data secure but still allow calculations on it (like in cloud services)?
- What’s new? Homomorphic encryption allows people to work on encrypted data without needing to decrypt it, ensuring privacy.
3. Zero-Knowledge Proofs (ZKP)
- What’s the problem? How can you prove you know something without revealing the information itself?
- What’s new? Techniques like zk-SNARKs and zk-STARKs are being used in blockchain to prove transactions and keep them private.
4. Blockchain and Decentralized Cryptography
- What’s the problem? How can we create secure, trustless systems for transactions?
- What’s new? Cryptography is critical in blockchain, using methods like elliptic curve cryptography (ECC) and Merkle trees to secure and verify transactions.
5. Lightweight Cryptography
- What’s the problem? Many devices like IoT gadgets have limited processing power, making traditional encryption too heavy.
- What’s new? Lightweight cryptography provides security for smaller, resource-limited devices, helping ensure safe communication in systems like smart homes.
6. Multi-Party Computation (MPC)
- What’s the problem? How can multiple parties compute something together while keeping their individual data private?
- What’s new? MPC allows people to share and compute data securely without revealing it. It’s useful in areas like finance or voting systems.
7. Passwordless Authentication
- What’s the problem? Passwords are often weak and can be easily hacked.
- What’s new? Systems like FIDO2 and WebAuthn use cryptography to enable secure logins without passwords, using methods like biometrics (fingerprints) or special devices instead.
8. Quantum Key Distribution (QKD)
- What’s the problem? In the future, even secure key exchange could be at risk from quantum computers.
- What’s new? QKD uses the principles of quantum physics to create keys for encryption, making them extremely secure against hacking.
9. Elliptic Curve Cryptography (ECC) Advancements
- What’s the problem? We need strong encryption that doesn’t require large keys, as large keys slow things down.
- What’s new? ECC continues to be refined for better efficiency, and used in blockchain and secure messaging. It provides strong security with smaller keys.
10. Privacy-Preserving Cryptography
- What’s the problem? How can we analyze data while keeping people’s personal information private?
- What’s new? Techniques like differential privacy allow data analysis without exposing personal details, which is helpful in fields like healthcare and marketing.
Conclusion
Cryptography and cryptology are both essential in today’s digital world, but they serve different purposes. Cryptography focuses on creating secure methods to protect data, while cryptology covers both the creation and the analysis or breaking of these methods.
Cryptography is vital for securing online transactions, messaging, and sensitive communications. On the other hand, cryptology ensures that these systems are continually tested and improved, playing a crucial role in cybersecurity and intelligence efforts.
As technology advances, particularly with the rise of quantum computing, both cryptography and cryptology will need to evolve to stay ahead of potential threats. Post-quantum cryptography and Zero-Knowledge Proofs are two of the exciting areas where these fields are advancing.
In summary, while cryptography protects our data, cryptology ensures we remain one step ahead of attackers by analyzing and improving these protections. Together, they form the backbone of modern data security, keeping our information safe in an increasingly connected world.
