Table of Contents

Are we ready for the quantum computing revolution after all? With technology advancing at breakneck speeds, quantum computers keep revealing more and more fundamental flaws in our classical cryptography techniques. A vital antidote, Quantum-Safe Cryptography, provides strong protection against such impending attacks.
Because industries rely heavily on secure digital communications, they must urgently transition to encryption methods that can withstand quantum attacks. In this article, we’ll explain what it is, how it works, why it matters, and how it protects your digital future in a quantum-powered world.
Understanding the Core of Quantum-Safe Cryptography
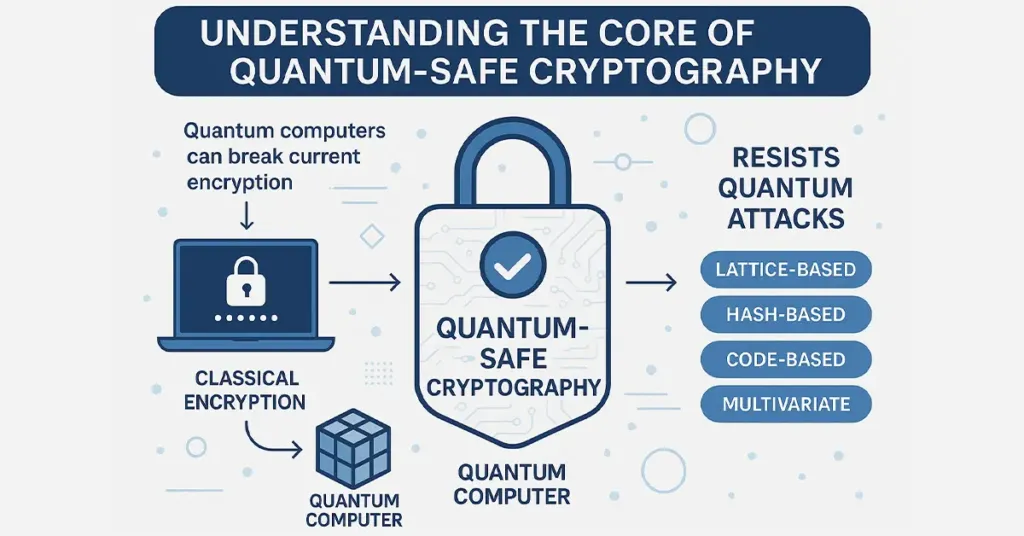
Quantum-Safe Cryptography encompasses new-generation cryptographic protocols that resist extremely powerful quantum computer-based attacks. While current computers struggle to break complex math problems, quantum computers can break standard encryption methods like RSA and ECC within seconds. This groundbreaking capability forces cybersecurity experts to reassess plans for encryption.
Developers counter the threat by creating algorithms from problems that quantum computers are wasteful at solving. They include lattice-based, hash-based, code-based, and multivariate polynomial schemes. They all fortify digital security with long-term confidentiality and integrity, even in a future quantum-enabled world. As computing becomes quantum, embracing encryption that can withstand its might is no longer a technical necessity but also a strategic initiative to protect confidential data and provide confidence in digital systems.
The Need for Quantum-Safe Cryptography in Post Quantum Security
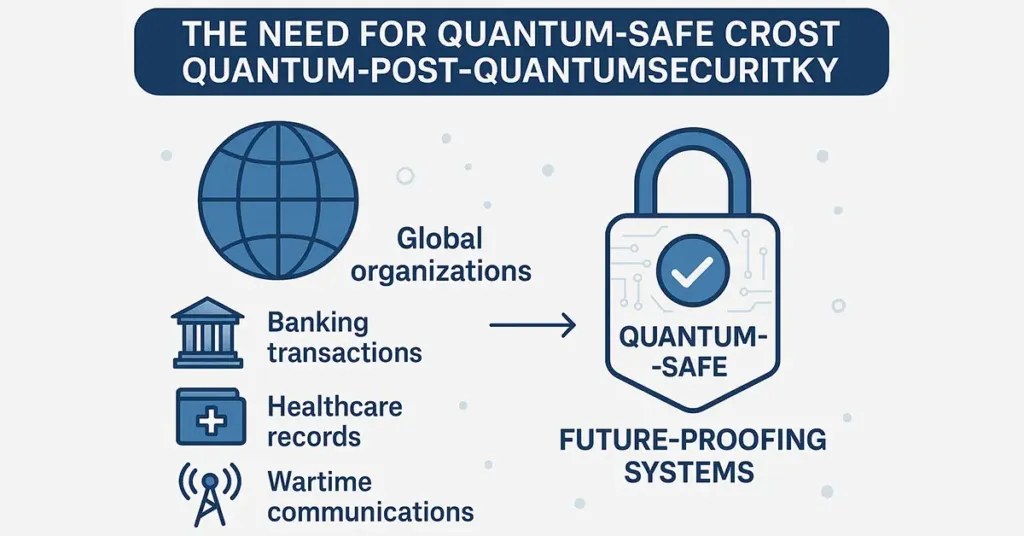
As post quantum security concerns mount, global organizations scramble to protect their sensitive information. These sensitive sectors, like banking transactions, healthcare records, and wartime communications, all depend on encryption methods that represent a future means of circumvention for quantum computers. Quantum-Safe Cryptography offers an anticipatory, proactive solution that operates to pre-empt and render powerless these future threats before they can harm.
Moving to this new-generation approach to encryption isn’t just a move to newer, more powerful technology; it’s future-proofing entire systems so that confidentiality and integrity are ensured in a quantum-enabled world. Governments and businesses need to begin incorporating these secure cryptographic techniques now to better safeguard against threats and have secure digital operations well into the next decade. Taking action early remains essential to enabling good post-quantum defense.
Building a Quantum Resistant Blockchain with Quantum-Safe Methods
Quantum attacks attack blockchains directly since such systems heavily depend on cryptographic signatures to make transactions and authenticate identities. To protect against this kind of threat, developers implement quantum resistant blockchain by incorporating Quantum-Safe Cryptography into their fundamental architecture directly. Adopting quantum-resistant algorithms, such blockchains maintain key properties such as data integrity, immutability, and decentralization even against highly capable quantum attackers.
Prominent blockchain initiatives dynamically explore and apply Quantum-Safe Cryptography best practices to secure digital signatures, hash functions, and consensus algorithms from hypothetical quantum attacks in the future. As the risk of quantum computing evolution persists, securing decentralized financial ecosystems and other blockchain solutions has emerged as a necessity for developers and organizations. These practices ensure blockchain technology is safe and robust after quantum, with users’ assets and data secured from new quantum attacks.
Advances in Post-Quantum Cryptography Algorithms
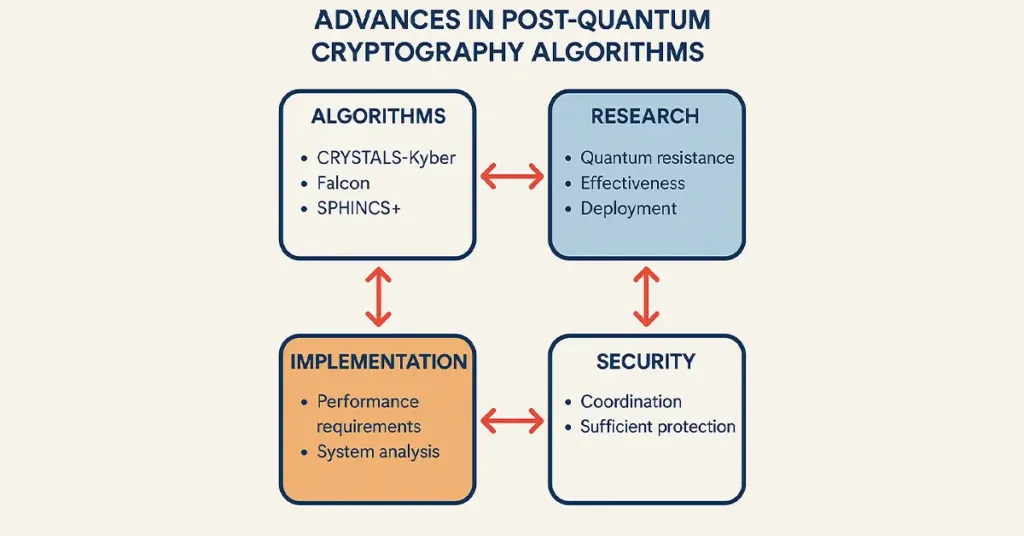
Advancements made by researchers in post-quantum cryptography are helping move the technology towards putting it into practice safely. Currently, CRYSTALS-Kyber, Falcon, and SPHINCS+ have a strong chance of adoption into the NIST Post-Quantum Cryptography Standardization process. Various tests by researchers look into the quantum resistance, effectiveness, and possible deployment of such algorithms.
Organizations face intimidating choices while implementing such new cryptographic algorithms, balancing performance and security requirements. System requirement analysis and infrastructure compatibility are two issues that must taken into consideration while choosing the algorithm. The developers and security teams have to coordinate with each other to ensure that the selected algorithms will offer sufficient security without introducing excessive disruption or overhead. These continuing developments in cryptographic algorithms provide a way forward for safe migration into the post-quantum era, and they help protect data and communications against quantum attacks in the future.
How Quantum Technology Challenges Traditional Security
Quantum technology introduces its game-changing abilities like superposition and entanglement that threaten mainstream security systems in their existence. With these abilities, quantum computers can handle and solve complex mathematical equations much faster than mainstream computers, making most mainstream security mechanisms out of date. Traditional public-key encryption is dependent largely on factoring large primes or discrete logarithms—schemes that quantum computers can do at high speeds, rendering such types of encryption useless in just seconds.
Such ability compromises the confidentiality and integrity of sensitive information within various industries, such as finance, health care, and government communications. In order to circumvent this difficulty, researchers and programmers have created new cryptography methods that are difficult to crack with the use of quantum computers.
Such new cryptography methods, known as Quantum-Safe Cryptography, employ hard mathematical problems that quantum computers cannot decrypt. With the use of such secure algorithms, businesses can keep their data safe from the emerging threat posed by quantum computing, hoping that their security system will remain reliable despite the acceleration of the rate of technological progress.
Adopting Quantum-Safe Cryptography in Government and Industry
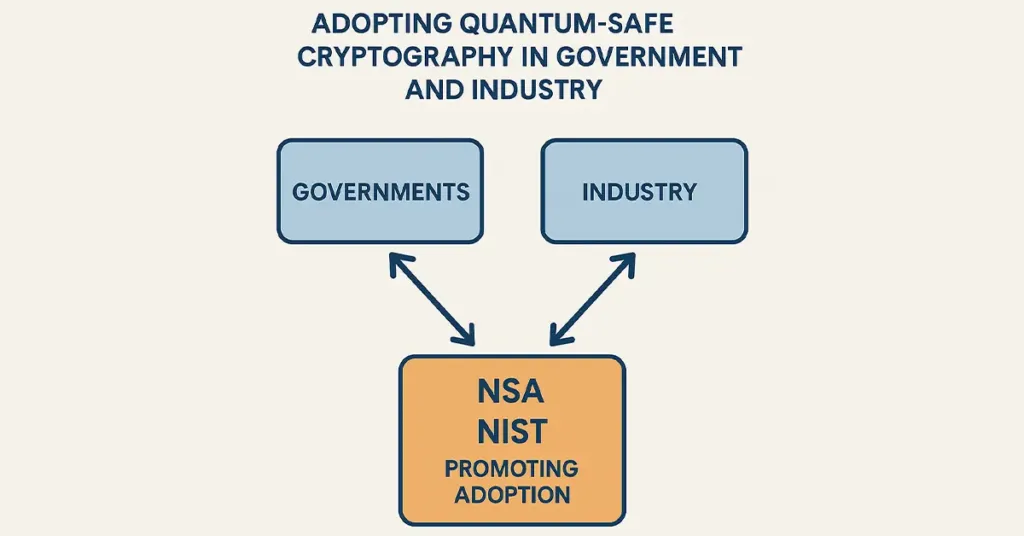
Governments, as well as industries, are quick to see the serious threats quantum computing represents to today’s security infrastructure. The National Security Agency (NSA) and National Institute of Standards and Technology (NIST) are eagerly promoting the adoption of Quantum-Safe Cryptography as early as possible in an attempt to preserve national security and secure sensitive information in the private sector.
Banks, physicians, and major technology firms are already thinking through their current stakes in cryptography to determine which are vulnerable to quantum computer cracking. The companies are also working on overall migration plans to move their encryption schemes to quantum-resistant algorithms.
Working towards Quantum-Safe Cryptography will help banks and businesses avoid major breaches that could cause the public to lose faith. With Quantum-Safe Cryptography in place, governments and industries can now secure their information for a much longer period than they used to.
While quantum technology progresses further, institutions that implement these next-gen cryptographic solutions in the future might suffer atrocious consequences like data breaches and financial loss. Thus, public and private sectors alike must approach security in this fast-evolving world of technology with a strategic, long-term perspective.
The Role of Quantum Blockchains in Future Networks
Quantum blockchains integrate the decentralized benefits of conventional blockchain technology with the ultra-high security features of Quantum-Safe Cryptography. When the two technologies are combined, digital ledgers become impenetrable and safe from attacks by highly sophisticated quantum computers. Developers may make blockchain networks more resilient to the constantly changing quantum threats by implementing quantum-resistant algorithms. This hybrid model ensures confidentiality of sensitive information and transaction integrity in place, a fundamental aspect to foster trust among stakeholders and consumers.
The function of quantum blockchains goes well beyond elementary security enhancements. All industries like finance, healthcare, and supply chain management depend on secure, open, and unalterable records. Quantum blockchains protect these records from quantum-capable attacks that otherwise breach data confidentiality and system stability. For instance, in finance, quantum blockchains can protect advanced transactions and digital assets and protect against fraud and unauthorized use. In healthcare, they protect patient data, keeping it confidential and compliant with regulations. In supply chain management, quantum blockchains increase traceability and reduce counterfeit product or data manipulation risk.
With the improvement of quantum computing capabilities, existing blockchains are increasingly vulnerable. Existing encryption schemes will ultimately not be able to withstand quantum attacks, threatening decentralized networks. Preemptive measures such as quantum blockchains foretell the issue by applying quantum-resistant cryptography algorithms from the beginning. By taking action early, blockchain design becomes future-ready and keeps organizations safe while reaping the benefits of being on the blockchain.
FAQs
1. Describe Quantum-Safe Cryptography?
These cryptographic techniques are difficult for quantum computers to decipher. They take over from RSA and ECC, as the old approaches will not be of use once quantum technology becomes mainstream.
2. Why is Quantum-Safe Cryptography important?
We must begin using new methods to protect data when using quantum computers, since they will eventually be able to crack legacy encryption.
3. When should organizations implement Quantum-Safe Cryptography?
Organizations must implement new encryption protocols now to secure their systems many years before quantum computers are ever commercially available, so they are safe from future quantum-based cyber attacks.
4. What are the primary categories of Quantum-Safe algorithms?
Lattice-based, code-based, multivariate polynomial, and hash-based approaches are the main types of these algorithms. Every one of them has advantages, but there are also trade-offs in terms of performance and security.
5. Will existing encryption standards become obsolete?
Yes, as quantum computers get stronger, it will become necessary to entirely switch to different security methods since existing encryption methods will be broken.
6. How can I migrate to Quantum-Safe Cryptography?
Evaluate all your current systems to understand their weak points, then train and put in place new types of quantum-resistant cryptography to securely move systems to the new technology.
7. Are there established practices for Quantum-Safe Cryptography?
Institutions like NIST are continuously strengthening and standardizing new cryptographic standards. Governments and firms embrace these standards preemptively to enhance defenses against future quantum attacks on computers.
8. What is post-quantum cryptography?
Post-quantum cryptography aims to design algorithms that will protect communication against quantum computers, as soon as these can be built and crack current techniques.
9. Is Quantum-Safe Cryptography computationally intensive?
Some algorithms use enormous amounts of computer processing, and this slows down systems. But scientists toil day and night to make such algorithms simpler so that they are more efficient without losing strong security against the evolving threats.
10. Can individuals adopt Quantum-Safe Cryptography?
Individuals can shield their private data with state-of-the-art cryptographic techniques as programs applying these new security protocols become prevalent and user-friendly enough to make them usable for common digital privacy requirements.
11. What is the role of NIST in all this?
NIST takes the lead in creating and standardizing next-gen cryptographic protocols, providing robust frameworks and guidelines adopted by organizations and governments to strengthen their cyber protection against mounting threats.
12. How does it affect blockchain?
Next-gen cryptography secures blockchain networks via protection of digital signatures and consensus algorithms, fortifying these decentralized systems against potential attacks with available quantum computing powers.
13. Are there any commercial products that are supportive of Quantum-Safe Cryptography?
There are several companies that create and sell VPNs, messaging applications, and secure communication software that utilize advanced cryptographic methods to shield consumers from future quantum computing threats in real-time digital transactions.
14. How imminent is the quantum threat?
Quantum computers that can crack existing encryption systems are not yet ubiquitous, but insiders say they will be within a decade, and so the need for organizations to start planning now.
15. What is a quantum-resistant blockchain?
A quantum-resistant blockchain leverages newer, quantum-proof cryptographic methods that cannot be compromised by high-end quantum computers, keeping transactions and data secure even if quantum technology comes to dominate our existence.
16. Is AI vulnerable to Quantum-Safe Cryptography?
Yes. Securing AI communications and data training requires robust quantum-computer-proof encryption techniques, keeping AI systems intact and trustworthy as the digital world changes.
17. Which sectors are hit the hardest?
Finance, healthcare, defense, and infrastructure industries are most severely impacted. All these industries need a high volume of secure communication and data, and hence are top targets for ahead-of-time encryption to safeguard them against quantum attacks in the future.
18. Is Quantum-Safe Cryptography open source?
Yes. Developers regularly maintain several open-source libraries that support quantum-resistant algorithms, providing ready accessibility and collaborative efforts to further improve security against potential quantum computing attacks.
19. Does Quantum-Safe Cryptography have any impact on data transmission speeds?
Some of them do slow down data transmission speeds slightly, but continuing optimisations and improvements attempt to reduce such an effect to the absolute minimum to provide secure communication with negligible performance penalty.
20. What is the potential and outlook for Quantum-Safe Cryptography?
Thanks to quantum computing, using safe algorithms to prevent quantum attacks will become common, ensuring that all global businesses are kept safe in their data and communications.
Conclusion
Quantum computing introduces unavoidable risks to the current digital infrastructure. The transition to using Quantum-Safe Cryptography is something both users and companies need to accept as critical. To protect important information, communications, and key systems from threats brought by quantum computers, we should take swift action now. Users and organizations make themselves safe against quantum computers by implementing Quantum-Safe Cryptography. Acting now enables us to have a strong digital future that will remain secure and reliable for generations to come, with privacy safeguarded and confidence in future technology.
References-
(Stephanie Susnjara, What is quantum-safe cryptography?)
(Sal Kimmich, Post-Quantum Cryptography: Preparing for a Quantum Future)
(Carl Windsor, Quantum-Safe Encryption: Safeguarding Data for the Quantum Era)
