Table of Contents

What becomes of our digital life when supercomputers are commonplace? In this situation, experts rely on a field known as quantum security. The more quantum technology that is being invented, the way we defend against sensitive information is also under examination. Encryption techniques currently in place can be made redundant within the next few years. Remaining ahead of the threat posed by supercomputing requires quantum security. This article explores how quantum security is changing the future of data protection and securing systems more than ever.
The Threat to Current Cryptographic Algorithms
Current cryptographic algorithms depend a lot on mathematical problems that it is practically impossible to break using conventional computers. Current algorithms of encryption, like RSA and ECC, depend on the assumption that factoring large numbers or solving discrete logarithms will take thousands of years. Quantum Computers destroy this assumption. These computers can execute calculations at light speed and are capable of breaking these conventional systems within seconds. Therefore, present-day encryption methods will be obsolete and extremely vulnerable very shortly.
To address these threats, quantum security has become a pressing need at once. Quantum security brings in new systems that are quantum-resistant to attacks. Quantum cybersecurity is aimed at setting up new mechanisms to encode, transmit, and decode information securely despite quantum attackers. Governments, research centers, and technology companies have begun to invest heavily in quantum cybersecurity solutions. Their rationale is straightforward: adopt future-proof security solutions in the present, before Quantum Computing can release its threat.
Introducing Post-Quantum Cryptography
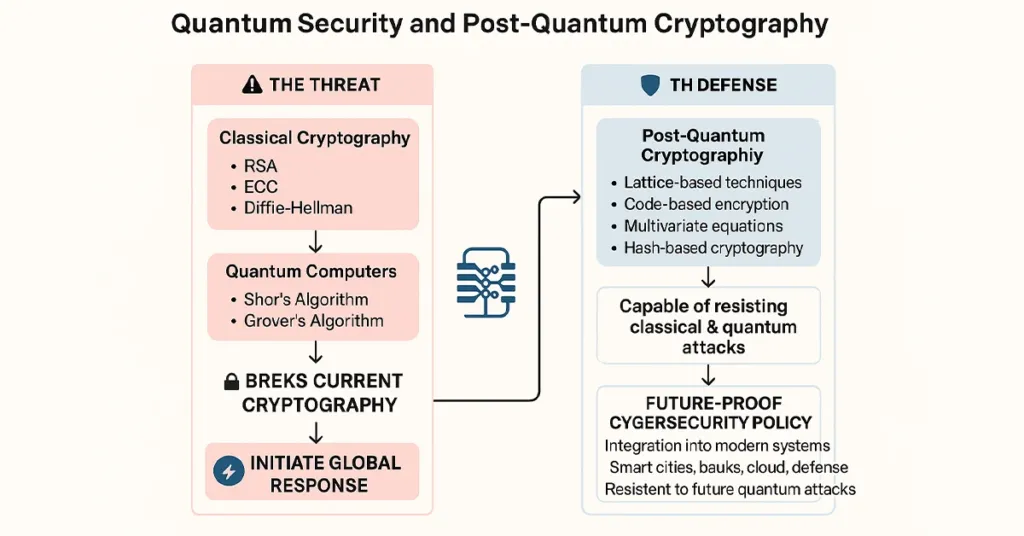
Quantum security is no longer a distant concept—it’s soon to be the foundation of global cybersecurity policy. As Quantum Computers are developing, they will make old cryptographic systems redundant. To counter this, researchers and cybersecurity professionals are working on a revolutionary method called Post-Quantum Cryptography. This discipline is all about creating encryption methods that are safe even against future quantum machines.
Unlike traditional techniques like RSA or ECC, Post-Quantum Cryptography is based on mathematical problems difficult for quantum computers to perform. These include encryption techniques based on lattices, hashes, codes, and multivariates. All these techniques provide immunity against both classical and quantum computational attacks.
Government leaders and international institutions are not taking this shift lightly. The National Institute of Standards and Technology (NIST) has already started to choose and certify the best quantum security algorithms through an ongoing multi-year process. This is a full turnaround in the approach that the cybersecurity community understands protection for digital things—no longer as a dash to be the quickest but as a call for improved smarter defenses.
By integrating Post-Quantum Cryptography into the systems of today, we can create a secure digital world that can withstand even in the age of Quantum Computing.
NCOG is implementing these post-quantum concepts and creating blockchain infrastructure that is ahead of its time in terms of cryptographic security.
The Power and Risk of Quantum Computers
Compared to classical computers, quantum computers operate on completely different principles. Rather than binary bits being 0 or 1, Quantum Computers utilize quantum bits—or qubits, which exist in more than one position simultaneously because of superposition and entanglement. Quantum Computers can hence compute many calculations at the same time, solving complex problems much faster than any classical computer.
While this computer capacity brings science, medical, and artificial intelligence advancements, it also brings gigantic risks. Quantum Computers can be used by ill-intentioned parties to crack existing cryptography systems protecting everything from bank transfers to government information and personal data. Fear of cracking digital trust has fostered an extreme need for quantum security solutions.
Among the worst is the “harvest now, decrypt later” strategy. Already, encrypted data has been being gathered with intent to decrypt it when Quantum Computers are powerful enough. This pending threat puts today’s secret communications and sensitive records to risk.
To prevent this, quantum security is focused on creating a defense that is quantum attack-proof. We can ensure our quantum-resistant digital infrastructure continues to be safe even as Quantum Computing is heavily advancing by acting now.
The Role of Quantum Computing in Cyber Defense
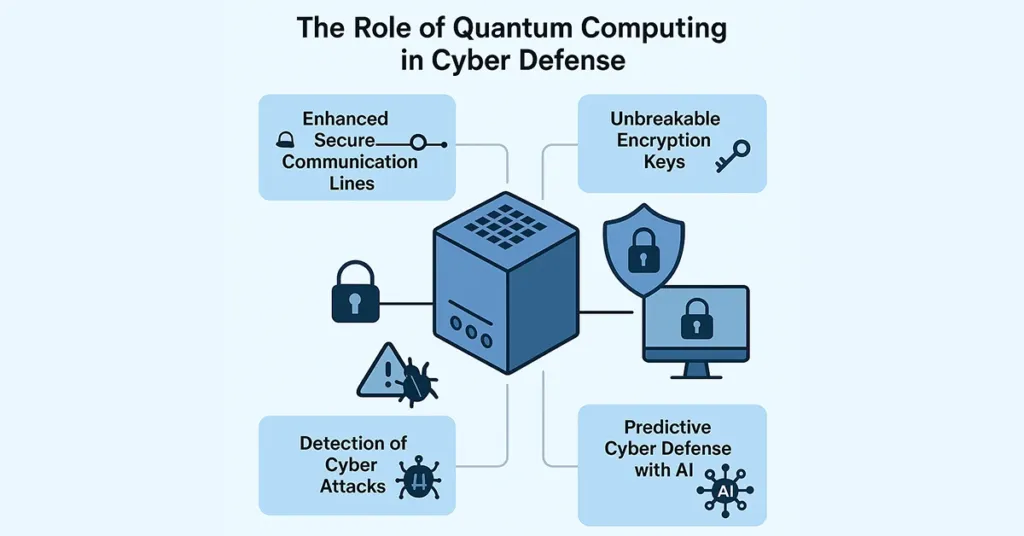
Despite its danger, Quantum Computing is also an immense asset in enhancing cybersecurity. The same technology that can potentially destroy traditional encryption is being utilized by security engineers and researchers to create stronger, next-gen defensive systems. Quantum Computing can make communication lines even more secure, produce unbreakable encryption keys, and identify cyber attacks at an early stage, in time to prevent damage.
In the never-ending struggle between hackers and cybersecurity professionals, quantum security assists in tilting the scales in favor of protection. Giants in the tech sector including Microsoft, Google, and IBM, are actively investing in quantum security technologies. These technologies are used to observe huge sets of data in real-time, alert on suspicious behavior, and respond in real-time to malevolent activity. They also create secure cryptographic keys using the Quantum Key Distribution method, which is extremely resistant to being intercepted or stolen by hackers.
With artificial intelligence built into it, quantum security is even more potent. They together provide predictive and adaptive defense measures that neutralize developing threats before they attack. They differ from old systems that retaliate only after an attack, as quantum security systems actively guard digital territories.
Through this means, quantum security is not a passive defensive technique—it is an active toolbox that can scan, evolve, and counter emerging cyber threats at unprecedented speeds and levels of intelligence.
Leveraging Quantum Key Distribution
Quantum key distribution is the state-of-the-art use of quantum security. Classical key exchange protocols are based on mathematical challenges, but QKD uses the very foundations of quantum mechanics to make it possible to have ultra-secure communication. Encryption keys are sent through a quantum channel as quantum particles—most commonly photons—in QKD.
The particles are in fragile quantum states that will collapse or become distorted upon measurement. What this means is that any attempt to intercept or tap into the key exchange process immediately changes the quantum particles’ state, alerting the receiver and sender to the possible breach of security.
This intrinsic capacity for interference detection makes QKD quite possibly the most secure key distribution method ever devised. It shifts our paradigm for thinking about digital security—not merely something to encrypt but something to observe and guard at the fundamental level. In combination with the usual encryption techniques, QKD makes the key exchange procedure fully tamper-proof and reliable.
Quantum security technologies such as QKD are now being deployed on pilot networks in Asia and Europe. Governments and industry are piloting QKD on high-security applications, including financial transactions, secure messaging, and military defense communications. While QKD is still expensive and dependent on special hardware as of now, research and development are reducing costs.
As the technology keeps advancing, QKD will increasingly become even more accessible and scalable from niche pilots to business as usual. This will significantly support the integrity and confidentiality of digital infrastructure in various industries. By facilitating a new norm in secure communication, quantum security based on QKD is a groundbreaking step forward in safeguarding the world’s data infrastructure against future attacks, particularly those by Quantum Computers.
Real-World Implementation of Quantum-Safe Cryptography
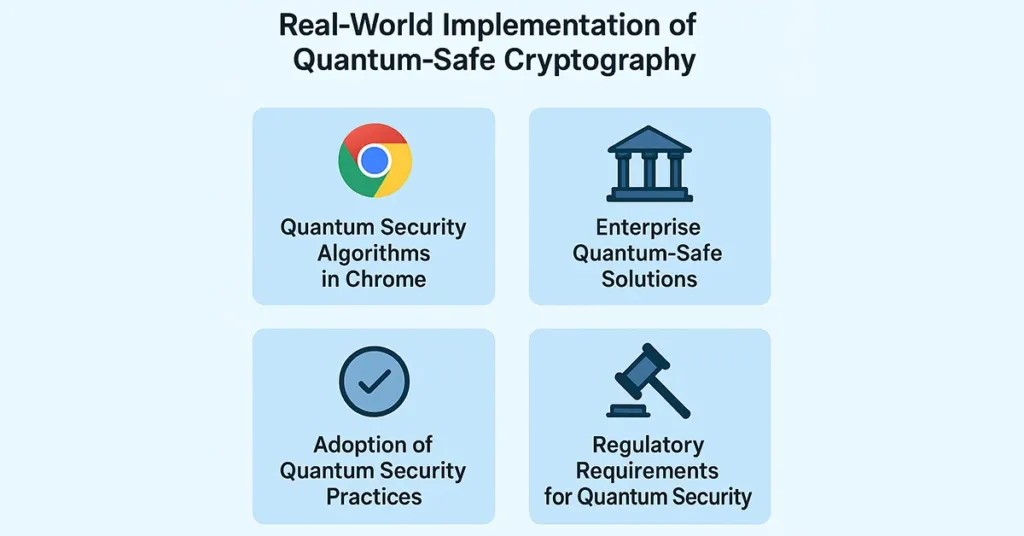
Quantum-Safe Cryptography is rapidly transitioning from theoretical study to practical application. Large technology firms have already started incorporating quantum security into their services and platforms. Google, for example, has experimented with quantum security algorithms within the Chrome browser for benchmarking their performance on real-world internet communications. The first tests are intended to allow users to easily switch to post-quantum encryption without sacrificing performance or user experience.
IBM has gone the enterprise route. IBM has introduced an enterprise-grade suite of quantum security solutions. They have software libraries, development kits, and hardware security modules that are Post-Quantum Cryptography-enabled. IBM is educating clients on how to get systems and data ready for a world where Quantum Computers can break current encryption with ease.
These practical applications prove that quantum security is no longer a far-fetched, otherworldly concept—it is now an urgent business imperative. Progressive businesses now recognize that implementing quantum security solutions is required for safeguarding customer confidence, compliance, and long-term asset security.
Governments and regulatory bodies are also gearing up for the transition. More than ever before, imminent cybersecurity laws will likely require the use of quantum security practices, particularly in industries such as healthcare, defense, and finance. Those businesses that get started early in deploying quantum security solutions will not only be ahead of the compliance game but will also have a key competitive advantage. Quantum security leaders will set the pace in data protection. They will assure customers, investors, and partners that they are quantum future-ready.
Building Trust with Quantum Encryption
Quantum Encryption is a radical advance over the old cryptography techniques. Unlike classical encryption, which makes use of knotty mathematical puzzles, quantum encryption uses the general ideas of quantum mechanics to produce virtually unhackable codes. As such, it is one of the most exciting and potentially most useful fields of research in the field of quantum cybersecurity.
Quantum encryption is based on the use of quantum states, such as entangled photons, to encrypt information. Entangled photons are in an entangled state so that any measurement or intercept will destroy their quantum state instantly. This sabotage functions as an alarm, signaling the receiver and sender of the possible interception of the channel. This inherent property of quantum encryption protocols makes it possible for them to detect eavesdropping in real-time, providing security that cannot be obtained using classical encryption.
Government authorities and financial institutions have realized the absolute need for this technology. A few are already piloting quantum cybersecurity models using entangled photons to safeguard their most secure communications. These pilots show how quantum encryption can render secure messaging virtually unbreakable. With the application of quantum concepts, these institutions make any intercepts by an unauthorized party not just detectable but also render the attacker unable to derive useful information.
As quantum networks grow, quantum cybersecurity will increasingly be the foundation for building and sustaining digital trust. In a society where data breaches and privacy encroachment become more sophisticated, quantum encryption provides a completely new foundation for communication security. It will secure not just messages but also key transactions, contracts, and digital identity.
Industry Adaptation to Quantum Cybersecurity

Financial Sector Takes the Lead
The financial community is the first to respond to the increased needs of Quantum Cybersecurity. Banks, investment banks, and payment systems use strong encryption heavily to protect transactions, customer information, and trade secrets. The quantum threat to traditional encryption motivates these mechanisms directly. Financial institutions are, in response, conducting extensive risk analyses directed toward quantum vulnerabilities and implementing quantum cybersecurity procedures to protect their networks.
Certain companies are already experimenting with Post-Quantum Cryptography in secure data transmission protocols. Others are teaming up with start-ups to experiment with Quantum Key Distribution (QKD) systems. These steps are indicative of the industry’s proactive stance toward future-proofing its web assets.
Healthcare Implements Security Steps
Health care workers work with some of the most personal information of all, and thus, they are prime targets for hackers. As concerns over Quantum Cybersecurity grow, hospitals, research centers, and pharmaceutical firms are shelling out money for quantum cybersecurity products. Defending electronic health records and drug trial information from quantum-based attacks is now a question of strategic imperative.
Some vendors are looking into hybrid encryption schemes that blend classical and quantum-resistant techniques. Others are adding quantum cybersecurity features to telemedicine platforms and patient data portals to allow for long-term confidentiality.
Defense and Government Drive Innovation
Governments and defense agencies are also exerting great efforts to enhance their cyber defense through quantum cybersecurity. The security of the nation relies on the trustworthiness of communications, sensitive data, and intelligence, all of which can be broken through future quantum attacks. Governments worldwide are emphasizing quantum research and are partnering with technology firms to create national quantum standards for cybersecurity.
A few already have implemented Quantum Encryption practices within test labs, with firm intentions to implement such measures at scale shortly.
Business Leadership Sees the Need
Corporate boards are increasingly making quantum cybersecurity a strategic imperative. Chief Information Security Officers (CISOs) are being asked by their leadership more and more if their company is ready for the quantum threat. Such leadership pressure is driving quantum cybersecurity implementations forward.
Simultaneously, quantum cybersecurity solution startups are seeing a surge in venture capital funding. Market momentum is reflecting growing awareness and urgency. Organizations understand that ignoring quantum cybersecurity today could mean greater exposure tomorrow.
How Quantum Security Protects Personal Privacy
Personal privacy is arguably the greatest concern in today’s digital age. Every day, individuals post enormous amounts of sensitive information on the internet—everything from bank account details to health records and private communications. Traditional methods of encryption have protected it all for decades. The advent of Quantum Computers threatens to undermine much of those systems and compromise personal privacy. That is where quantum cybersecurity enters as the great equalizer.
Quantum security guards individual privacy by employing the principles of quantum physics to establish forms of cryptography that are inherently immune to even the strongest quantum assaults. Classical encryption, which is mathematical complexity-based, operates differently from quantum cybersecurity, employing features like superposition and entanglement to shield information from outside intrusion.
One such pertinent technology is Quantum Key Distribution (QKD). QKD enables two parties to exchange encryption keys over quantum channels in a way that any eavesdropping attempt would alter the quantum state in real time. This notifies users of potential intrusion before their sensitive information is leaked. This mechanism offers privacy of sensitive data such as passwords, medical records, or financial transactions.
Second, quantum cybersecurity protects privacy for the long term. Data encrypted with classical techniques today may be insecure in the future with more advanced quantum computers. With quantum-protected systems, data is protected both currently and against future threats, except for retro decryption.
Governments and companies are now embracing the need for quantum security in safeguarding individuals’ privacy. Through the adoption of quantum-safe encryption techniques, they aim to develop trust among users and ensure the integrity of information within a hostile cyberspace.
The Future of Quantum Networks and Secure Communication
The quantum network is the future of digital communication because it represents cutting-edge technology that will deliver unprecedented security and velocity. Classical networks are distinct from quantum networks in the respect that whereas the former apply common technologies, the latter employ quantum mechanics technologies to move data in a manner that is inherently secure and eavesdrop-free. The new technology will revolutionize how people, institutions, and governments communicate and protect data.
Quantum Key Distribution (QKD) is the foundation of quantum networks that ensures secure key distribution based on quantum states like entangled photons. Any attempt at eavesdropping makes it detectable as soon as it’s attempted, securing the communication channel. As quantum networks grow, they will offer an unbreakable backbone for the internet, making data transfers quantum-proof against hacking by currently available or even yet-to-be-created quantum computers.
Pilot experiments at several places around the world demonstrate the practicality and viability of quantum networks. European, Asian, and North American countries are investing heavily in quantum communications infrastructure, building quantum fiber-optic connections between large cities. They seek to incorporate quantum security into legacy telecommunications infrastructure, gradually moving towards a quantum-secured internet.
Besides security, quantum networks can also enable faster and more efficient communication. Quantum entanglement enables instantaneous correlations between remote locations and may be the basis for new applications like quantum cloud computing and distributed quantum sensing.
The growth of quantum networks will drive innovation in several industries. Banking transactions, healthcare exchanges of data, and government communications will all be enhanced with better privacy and security. Quantum networks will also enable the creation of quantum encryption techniques, which will protect information from even the best cyberattacks.
Government Regulations and Standards for Quantum Security
With quantum technology progressing at a faster pace, governments across the globe are racing to standardize and regulate quantum security measures to stay ahead of the threat. This is because it is understood that quantum computers will make many of the presently employed encryption systems obsolete, compromising sensitive government, business, and individual information. Strict standards and regulations must be put in place to facilitate secure communication, secure critical infrastructure, and uphold national security in the new quantum world.
The Government’s Role in Quantum Security
Since governments must secure important data, vital infrastructure and military resources, they take a major part in quantum security. Most nations worry about the possible dangers of quantum computers and have therefore rolled out specific programs to use quantum-safe technologies. They will likely team up with schools, companies and foreign partners to enhance both research and adoption.
Primary Regulatory Agencies and Their Activities
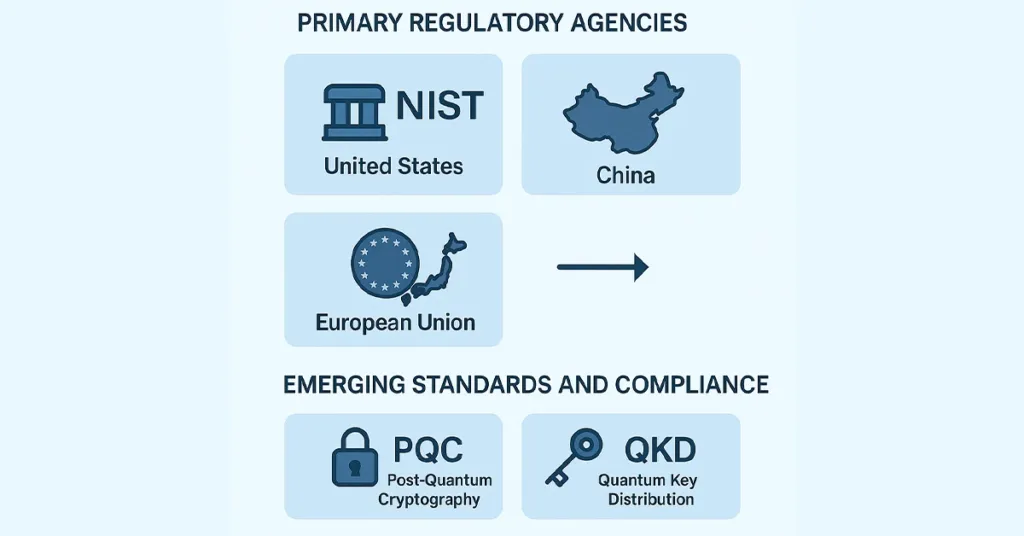
The strongest rule-making power in this area is likely the United States’ National Institute of Standards and Technology (NIST). NIST took the lead in post-quantum standardization by organizing an open competition to test and select quantum-resilient algorithms. The goal was to create a standardized collection of cryptographic algorithms that would be used to substitute for weak classical encryption schemes. There are regulatory frameworks in other nations, including China, the European Union, and Japan. The countries also possess quantum security research programs.
Emerging Standards and Compliance
Quantum security needs now revolve around post-quantum cryptography (PQC) and Quantum Key Distribution (QKD). PQC is a post-quantum attack-proof classical cryptosystem, whereas QKD uses quantum mechanics for secure key sharing. Standardization makes implementations interoperable, secure, and reliable between industries and borders. Governments are also establishing compliance guidelines to force organizations to plan for the quantum shift.
Challenges in Regulation
Quantum security is hard to govern because technology is spreading so rapidly, and there has to be coordination across the globe. In addition, it takes regulatory systems to become dynamic and flexible to achieve the balance between innovation and security. There also has to be action on issues related to privacy, quantum technology export controls, and geopolitical aspects.
Looking Ahead
Over the next few years, we should anticipate increased global cooperation and harmonized practices for quantum security. Governments would have a determining role in driving adoption, advancing research, and making sure that the public and private sectors are in a position to flourish in the quantum world securely.
Challenges in Deploying Quantum Security at Scale
Quantum security holds the promise of transforming the way we keep information secure against future quantum computer attacks. However, rolling out quantum security solutions on a massive scale across governments and industries is fraught with a particular set of challenges. These range from technical, economic, operational, and regulatory domains and make bulk adoption very challenging. It is only by knowing these barriers that organizations can begin to undertake a seamless transition to quantum-safe infrastructures.
Technical Complexity and Immaturity
Among the prime obstacles to quantum security scaling is the relative immaturity of quantum-safe technologies. In contrast to conventional cryptography, which has benefited from the luxury of decades of evolution and applied experience, much quantum security technology is experimental or pilot-scale. Lattice-based cryptography, code-based cryptography, and quantum key distribution (QKD) are only some of the algorithms that need further adaptation to run effectively on current hardware.
Quantum Key Distribution, on the other hand, depends upon quantum channels and bespoke hardware such as photon detectors and quantum repeaters. Current deployments of QKD also suffer from distance limitations and are cost-prohibitive. Furthermore, interfacing quantum hardware with classical networks remains a technical challenge. The vast majority of organizations cannot afford to retrofit or redesign their installed bases in a way that will allow quantum security solutions without incurring serious disruption.
Cost and Resource Constraints
It takes a large initial investment to achieve quantum security at scale. The cost of quantum-resistant hardware, software development, and specialist staff can be too great for small and medium-sized enterprises (SMEs). Quantum security is obtained by using specialist hardware for QKD and high-performance computing facilities for the application of new cryptographic algorithms.
Additionally, quantum security requires ongoing research and development to keep pace with developing threats and requirements. This requires sustained funding, which may not be feasible for every organization. Therefore, most companies are not willing to invest in quantum security until there are more concrete economic benefits or regulatory drivers.
Integration with Legacy Systems
Most organizations possess huge IT infrastructure developed over decades and often including legacy systems based on traditional cryptographic practices. Integrating quantum security into these diverse environments is an enormous challenge. Organizations must design hybrid systems that enable both classical and quantum-safe algorithms in the transition phase to maintain backward compatibility and set the ground for complete quantum readiness.
This phased deployment demands careful planning, vendor testing, and good cryptographic key and certificate management. Integration faults would result in weakness or failure of systems. Thus, having unfettered interoperability between new and old security systems introduces levels of operational complexity.
Lack of Standardization and Regulatory Frameworks
While advances in this regard are ongoing, quantum standards and regulations remain rolled out. The National Institute of Standards and Technology (NIST) has made strides in the form of issuing competitions for identifying quantum-resistant algorithms, but standardization remains undone and is not even yet generally accepted.
Without harmonized standards, companies have no idea what technology they should invest in. Without harmonized regulations, compliance is difficult and heightens the potential for incompatible or fragmented quantum security implementations. The regulatory agencies worldwide are also uneven in their quantum security readiness, which becomes complicated for multinational companies with uniform security policies.
Skills Shortage and Awareness Gap
Quantum security is an extremely technical arena that calls for the services of quantum physics, cryptography, and cybersecurity. Few such multi-disciplinary professionals exist as of now. Businesses need to spend money and time training or recruiting fresh talent, both of which entail a significant cost and delay.
In addition, quantum security urgency awareness is still limited to external specialist communities. Decision-makers undervalue the threat of quantum computers or delay because they need to address their other priorities. A delay in recognition stops strategic planning and holds back necessary investments.
Future-Proofing Against Unexpected Threats
Quantum computing itself is evolving rapidly. New algorithms, improved hardware, or quantum error correction advances may alter the security landscape in some unforeseen manner. This renders it uncertain what quantum security techniques will prove to be long-term effective.
Organizations thus need to create dynamic quantum security infrastructures that are capable of adapting or changing cryptographic algorithms on a case-by-case basis. Creating such flexible systems creates additional complexity and involves proactive cybersecurity.
Conclusion
Quantum security is now a reality, not a science fiction dream. It’s the basis for a safe online future. As Quantum Computers become more powerful, so will the demand for stronger protection. Companies, governments, and citizens must take action now. Placing quantum security in will provide long-term protection from future cyber/structures. With intelligent strategy and early implementation, future data defense will be secure, quantum-safe, and trusted.
FAQs
What is quantum security?
Quantum security is the security of digital information by the rules of quantum mechanics. It includes techniques and technologies aimed at protecting information against traditional and new quantum-based cyber threats. In short, quantum security seeks to develop encryption codes and communication protocols that will be immune even to attack by quantum computers, which can solve some problems many orders of magnitude faster than conventional computers. The objective is to develop systems that will be immune to the peculiar threat presented by quantum technology.
Why do we need quantum security now?
Quantum computers are developing fast and may soon acquire the ability to crack common encryption codes, like RSA and ECC, used to protect the majority of online communication today. This impending menace requires building and deploying quantum security technology today to safeguard data long before high-performance quantum computers are prevalent. Staying ahead helps us transition seamlessly and entirely bypass a period of vulnerability when encrypted information is susceptible at will to intruders.
Why is quantum security different from conventional security?
Conventional security depends on intricate mathematical challenges difficult for traditional computers to efficiently solve. Quantum security uses principles of physics, i.e., quantum mechanics, to construct physically safer encryption techniques. This makes quantum security resistant to classical and quantum attacks because it’s based on physical principles rather than mere mathematical difficulty.
Is quantum security only for large corporations?
No. Although large corporations are at the forefront of adoption for now due to cost and valuable data, quantum security will become a necessity for small and medium-sized businesses, too. As technology advances and costs lower, quantum security will be something that anyone concerned about data privacy and being ready for attacks in the future needs.
What are quantum keys?
Quantum keys are cryptographic keys generated and shared based on quantum phenomena. Quantum keys are the foundation for secure communication in quantum security systems, particularly Quantum Key Distribution (QKD). Since quantum states are non-reproducible and cannot be measured without altering them, quantum keys have tamper-evident transfer of encryption keys, rendering interception invisible.
Are hackers already capable of hacking quantum systems?
None today. Hackers are gathering encrypted data today in hopes of decrypting it tomorrow when quantum computers are powerful enough. This is referred to as “store now, decrypt later.” Quantum security techniques guard against this by making data encrypted today so secure that it will be quantum-safe as well.
How far are we from mainstream quantum computers?
Experts indicate that properly functioning quantum computers that might undermine classical cryptography are 5 to 20 years out. It is an unspecified timeline, but one well worth preparing for simultaneously. Quantum security is a wise investment if performed early enough, permitting organizations to protect sensitive information before threats from quantum are an issue.
Provide instances of quantum-safe encryption?
Lattice-based, code-based,-based and hash-based methods are all types of post-quantum cryptography. These rely on mathematical problems conjectured to be quantum-resistant and form the foundation of quantum security solutions in development and standardization.
Is quantum security the same as quantum computing?
No. Quantum computing applies quantum mechanics to make calculations many orders of magnitude faster than traditional computers and thus potentially crack existing encryption. Quantum security applies quantum principles to encrypt data against such an attack. One to calculate, the other to protect.
What is Quantum Key Distribution?
With QKD encryption keys are sent using quantum particles such as photons. A quantum system such as light, is altered if someone eavesdrops on the message, so the change can be spotted by the communicating parties. The process safeguards the exchange of keys inherently and offers a foundation for quantum security.
Will quantum security replace all encryption?
Eventually, yes. When quantum computers become capable of cracking current encryption, quantum security standards will be the only way of ensuring data confidentiality.
Are governments using quantum security?
Yes. China, the US, Germany, and others are investing in quantum security to employ it for national defense, critical infrastructure protection, and communication security.
Is quantum security hackable?
The traditional methods of hacking do not apply to quantum security because of the underlying physical characteristics upon which it is based, including the no-cloning theorem and the disturbance of the state of quantum systems. This renders it practically impossible for hackers to clone or intercept encrypted data.
Is quantum security already available?
Yes, but largely in pilot or limited capacities. Enterprise software and certain government initiatives have already adopted quantum security measures, particularly QKD, to experiment with their application in real-world scenarios.
What is post-quantum migration?
It is the migration from classical cryptography to post-quantum secure cryptography algorithms. It is a transition to keep sensitive information confidential in the quantum age.
What are the principal problems of using quantum security?
The principal problems are high cost, technical sophistication, and compatibility with the current systems. These, however, are being overcome as technology improves and workable tools become more accessible.
Who dominates quantum security technology?
Leading the way in advanced cryptographic innovation are advanced technology firms such as IBM and Google, and advanced start-ups such as ID Quantique and PQShield. They are leading the innovation and developing next-generation solutions to safeguard information against future computing-based threats, which are fueling future secure digital communication worldwide.
How do I prepare for quantum security today?
Begin by scrutinizing your current encryption systems and plan for introducing next-gen, future-proof cryptographic methods step by step that can resist future attacks on computation. Planning makes things simpler and provides more robust data security as time passes.
Is there a quantum security threat?
As quantum security is relatively new, its standards are still being established. Poor implementation or abuses would run counter to its purpose, and so professional advice comes into play.
In which industries is quantum security most needed?
The highest-priority ones are the high-risk sectors of defense, healthcare, infrastructure, and banking, but all industries will ultimately require quantum security as threats emerge.
Is there a quantum security certification?
There aren’t official certificates yet, but organizations such as NIST are working on standards that will foster compliance and certification in the future.
Is quantum security implementable on existing systems?
Yes. Hybrid solutions allow integration without completely displacing current infrastructure, making change easier.
Does quantum security demand special hardware?
Some methods require special hardware, notably QKD, but the majority of quantum security can be handled by regular computing hardware.
How expensive is quantum security?
There is a wide spectrum of costs based on approach and size, but costs will fall as usage grows and technology advances.
Will quantum security put an end to passwords?
Not at all, but quantum security will improve the overall design of security involving password systems and authentication systems.
What is quantum entanglement in security?
Quantum entanglement, particles are joined in a way that the status of one instantly impacts the other at any distance. With this feature, QKD security protocols are able to uncover any intruder trying to sneak in.
What’s not important about quantum security?
Difficulty and cost can be obstacles. However, the high cost of security is well worth the constraints.
How do developers learn about quantum security?
Through education, certification, seminars, and continued studies. Staying current is key because the practice evolves at lightning speed.
Will quantum security evolve?
Yes. Just as with traditional cybersecurity, this discipline will evolve to counter new threats and utilize new technology advancements, so our defense continues to be effective against new threats. Innovation is the impetus for strong defenses in a constantly evolving online world.
Is it too soon to respond to quantum security?
No, it is not premature to move. Planning and having future-proof encryption methods in place well ahead of time is important to safeguard information well before speedy new computing technologies pose a serious risk. Anticipating ahead prevents future vulnerabilities.
References-
(James Dargan, What is Quantum Security and how does it Work?)
(JisaSoftech, Data Privacy in the Age of Quantum Computing: Is India Ready? )
(Courtney Goodman, Understanding Quantum Computing in Cybersecurity)
(Kevin Coleman, Quantum computing and cybersecurity: opportunities & risks)
