Table of Contents

What if your online identity weren’t stored in a central system anymore? A new model is changing the way we approach privacy. Decentralized ID is the pillar for a secure online identity. It gives users ownership of their identity.
It does away with third-party verification. It deletes the risk of data breaches. People want more control, and Decentralized ID gives it to them. It provides security and transparency. It is user data-protecting and cross-platform.
In this article, we explain how Decentralized ID works, why we need it, and how it will continue to shape online identity going forward.
Control your identity. Protect your data. End-of-life systems, say goodbye. This article explores how Decentralized ID secures your digital life. Watch it, put privacy, security, and trust in your hands.
Understanding the Basics of Decentralized ID
A Decentralized ID grants control of the users’ identity on the internet. It does not depend on a centralized authority.
Blockchain technology and cryptography hold this apparatus in place. Users seal up identity data in secure digital wallets. These wallets interact with applications and services as needed.
No password is needed for any new service. The users don’t need to log in again on a different platform. Rather, they utilize verifiable credentials.
They are issued by trusted issuers, like schools or employers. Each credential confirms a different fact, such as your name or job title.
Your wallet securely holds these credentials. When required, you provide only the necessary information. This hides your privacy and minimizes data exposure. You decide what to disclose and to whom.
The system facilitates trust establishment between users and service providers. It minimizes identity theft and data breaches. Decentralized identity secures online space as user-controlled and safe for individuals and organizations.
Why Traditional Identity Systems Fail
Classic identity systems depend on centralized stores. They have one database that holds millions of users’ accounts. Hackers attack them. When security is breached, sensitive information is exposed. Personal information is exposed. Identities are stolen.
The harm is extensive. Victims take months to regain access and restore their reputations. Centralized systems provide a single point of failure. Compromised, all the identities that they hold are at risk.
These systems also ignore user control. You cannot choose what information to share. You cannot track who gets to see your information. Your privacy remains at risk.
No transparency. Companies own your identity behind your back. Users depend on a third party for access and authentication.
Such a flawed design betrays trust in online systems. A Decentralized ID ends such reliance. It gives the user total control. People have their identity in their own hands. This change makes digital services and platforms more secure and more intimate.
How Decentralized ID Works
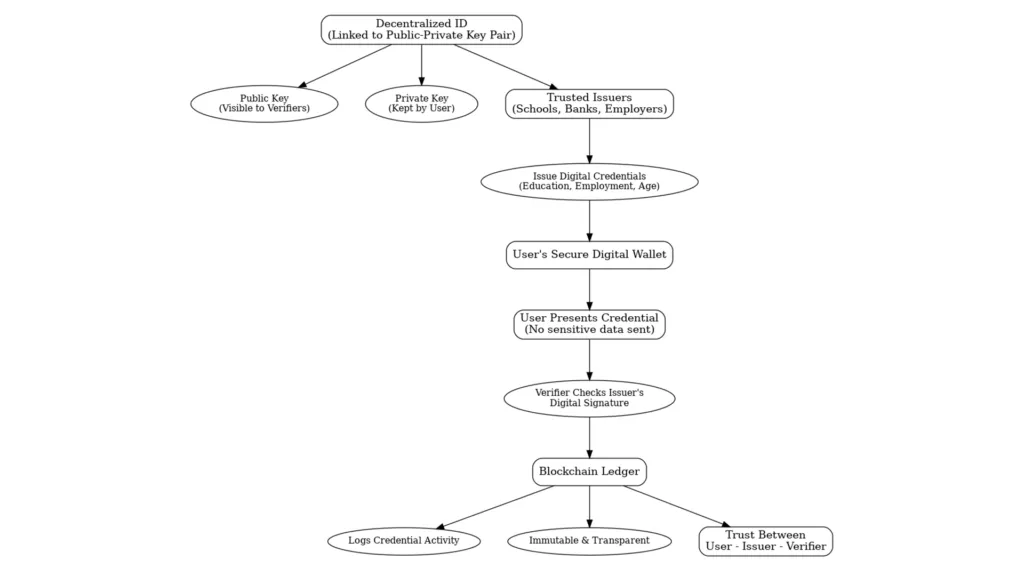
Every Decentralized ID belongs to the owner’s private data. It is linked with a public-private key pair. The public key is public. Verifiers utilize it to verify identity. The private key remains with the user. It secures access and makes data private.
If the trusted issuers are institutions such as schools, banks, or employers, then they issue credentials. Credentials verify certain information about an individual. They may verify education, employment status, or age.
Users place these credentials in a secure digital wallet. When they are required to establish identity, they present a credential. The verifier verifies the issuer’s digital signature.
No single sensitive data is sent in the process. Only the result of verification is transmitted. This preserves privacy.
The system employs blockchain to log credential activity. Blockchain makes the system transparent and unchangeable. It maintains records unalterably.
It helps establish trust between users, issuers, and verifiers. It constructs a safe methodology towards digital identity management.
Benefits of Decentralized ID
Decentralized ID ensures user anonymity and eliminates middlemen in identity handling. T, minimizing data exposure and abuse threats.
Users own their information. They decide what to reveal and to whom. This promotes transparency and trust.
The system is compliant with global privacy laws. It facilitates organizations in reaching levels of data protection legislation.
One identity can be used by users to access numerous services. Users do not have to remember an array of different usernames and passwords.
Credentials are simple to manage. End users control them directly with secure digital wallets.
Business saves money. Business no longer has to store enormous identity databases. Storage and security costs are reduced.
It also diminishes legal liability for data breaches. Customers grow more at ease, creating brand loyalty and trust.
It is a worldwide operation. It offers quick, safe, and real-time identity authentication.
It facilitates digital services innovation and cross-border trade. It empowers users and service providers.
Decentralized Tools That Power Identity Management
Decentralized tools enable secure and user-managed identity systems. It facilitates the creation, maintenance, and authentication of digital identities at scale.
Blockchain platforms are the building blocks. They hold records in an open and tamper-evident manner. This provides data integrity and assurance.
User credentials are held in digital wallets. Individuals use these wallets to securely present their identity in digital transactions.
Verification procedures verify credentials. They make sure that certified issuers issue the information. This prevents disclosing personal data.
Well-known techniques include uPort, Sovrin, and Veres One. They all facilitate identity creation and verification across several services.
They eliminate central databases. They restrict access to sensitive data.
They secure users from information breaches and unauthorized monitoring. Users remain in possession of their digital identities.
These technologies are used collectively in a decentralized system. They enhance identity management to be scalable, secure, and privacy-centered.
Decentralized ID relies on such technology to digitize spaces that have trust, privacy, and user empowerment.
Real-World Use Cases of Decentralized ID
This technology is transforming how individuals and organizations prove and manage identities worldwide. The following are the use cases of Decentralized ID-
Government and Education
Secure digital IDs are issued by governments, and it is easy to verify. Qualifications of students are confirmed in seconds. There is no need for physical certificates, and the process is accelerated.
Healthcare and Travel
Patients securely manage and control their medical information. Secure sharing with healthcare professionals. Digital passports are used by travelers for ease of crossing borders more easily.
Employment and Consumer Trust
Job applicants submit authenticated resumes to employers, minimizing fraud. Consumers authenticate sources of goods for quality and genuineness. This raises confidence in buying.
Inclusion in Developing Regions
Official documents are non-existent among the majority of individuals in developing countries. This system ensures identity, with individuals being able to access banking, education, and healthcare easily. It enhances social and economic inclusion.
Benefits to Businesses
Organizations apply this technology to secure onboarding and access. It facilitates compliance with regulations and the safeguarding of data. Organizations receive customer trust and enhanced security.
Decentralized Blockchain and Identity Security
Decentralized Blockchain provides the basis for Decentralized ID. Blockchain stores identity credentials securely. It is open. It makes data tamper-evident.
It prevents access by parties outside of the agreement. Each transaction is written down and verifiable. It removes central points of control.
This type is more robust. It is resistant to tampering. It creates trust. Blockchain presents a new breed of secure identity systems.
Challenges of Adopting Decentralized ID
All innovations come with challenges. Decentralized ID isn’t any different. Standardization is one of them. Not everyone follows the same rules. This tends to interfere with compatibility.
User education is also challenging. Individuals need to be taught how to utilize it. Private key loss is a great risk. Recovery is intricate when they lack sufficient backups.
Legal status is also changing. The governments and regulators will have to be involved in sustaining this new model. They need to establish proper rules. They need to provide users and data protection.
The Role of Decentralized Database in Identity Storage
A Decentralized Database facilitates storing identity-related information more easily. It removes central control. It increases data privacy. It guarantees data availability. These kinds of databases spread information across multiple nodes. It avoids losing data. It also provides scalability.
They are compatible with Decentralized ID systems. They keep references and metadata. They don’t keep sensitive information themselves. Decoupling enhances security.
Decentralized Architecture and Interoperability
Decentralized architecture is scalable for identity systems. It allows for integration with multiple platforms. It is suitable for global reach. It enables cross-border transactions. It improves service delivery.
Each component works autonomously. Identity wallets, blockchain ledgers, and verification processes work together in harmony. They build an end-to-end identity solution. Interoperability is the preference. Standards enable it. Initiatives like W3C and DIF encourage such standards.
Future of Decentralized ID
The future is promising. Governments are setting up a digital ID ecosystem. Tech players are creating more potent equipment. The ecosystem is expanding.
Decentralized ID will be in greater demand. It will enable smart cities. It will protect IoT devices. It will safeguard digital assets.
With adoption, growth comes in innovation. There will be new use cases. There will be new users. Secure digital identity vision will be realized.
Conclusion
Decentralized ID is revolutionizing identity management. It offers secure, user-managed access to digital services. With solid support of blockchain and advanced tools, it will revolutionize the digital space.
The greater the number of users who adopt this framework, the brighter and stronger the future of secure identity becomes.
FAQs
What is a Decentralized ID?
A Decentralized ID is a decentralized digital identity system. You entirely own your data. You decide what to share. No central authority decides your identity.
How is it different from traditional ID systems?
Traditional ID systems rely on central databases. Governments, banks, and large corporations are a few examples. Decentralized ID shatters central control. Blockchain and cryptography fill the gap.
What are some technologies that enable Decentralized ID?
Several technologies enable it. They are blockchain networks, cryptographic key pairs, digital wallets, and verifiable credentials. They all work together to provide secure and user-controlled identities.
Can it help prevent identity theft?
Yes. It minimizes the risk of identity theft. Your information is encrypted and in your control. Attackers can’t visit a centralized database and steal data.
Who are some entities that can issue credentials in a Decentralized ID system?
Issuers issue credentials. Governments, employers, health organizations, and schools are a few examples. All the credentials attest to some facts about you.
What if I lose my private key?
You can get locked out of your identity by losing your private key. Backup arrangements need to be put in place. Some systems employ recovery agents or social recovery schemes.
Is Decentralized ID legal to use?
Some nations are legally adopting and backing Decentralized ID. Others are creating laws and regulations. International legislation is being developed.
Can I use a single Decentralized ID on multiple platforms?
Yes. That is such an advantage. You can apply the same ID on various sites, apps, and services. It is easier to access without additional logins.
Is Decentralized ID secure?
It is very secure. It uses advanced cryptography and secure blockchain protocols. You decide who has access to it, reducing the risk of cyberattacks.
Are there any Disadvantages?
Yes. Disadvantages are a lack of international standards. Legal acceptance has not caught up. The technology is also unfamiliar to many users.
What is a verifiable credential?
A verifiable credential is an electronic proof. A party that one trusts issues it. It verifies information such as your name, education, or license.
Can Decentralized ID benefit businesses?
Yes. It lowers data storage and compliance fees. Personal data no longer needs to be stored by businesses. It also establishes trust with users.
How does it enable digital inclusion?
Millions of people do not have government IDs. Decentralized ID can provide them with secure digital identities. This enables them to use health, banking, and education services.
Is there a global standard for Decentralized ID?
Yes, the World Wide Web Consortium created it. The standards make IDs interoperable and trusted everywhere across the globe.
How can users control their identities?
Users control their IDs through digital wallets. Applications store and maintain credentials securely. You can access them using mobile or computer devices.
Why is Decentralized ID scalable?
Its decentralized nature enables it to scale. There can be more users and issuers without a limit. Blockchain technology can deal with big numbers efficiently.
Is Decentralized ID internet-connected?
Yes. You must be online to issue, verify, or renew credentials. Offline will happen eventually, but online is necessary now.
What do wallets do?
Wallets hold your digital credentials. You use them to prove who you are. They provide you with secure control over what you share.
Do I get to control who sees my data?
Yes. You have complete control. You choose what credential to present, when to present it, and to whom you present it.
Will Decentralized ID be a passport and license substitute?
Maybe. Governments will digitize IDs. Decentralized ID will eventually substitute for or supplement paper documents shortly.
References-
(Chayanika Deka, Decentralized Identity: The Future of Secure Digital Identity Verification)
(Devesh Patel, Revolutionizing Online Security with Decentralized Identity)
