The new concept ‘blockchain’ emerged in 2008 and was popularized in the community. People care about anonymity, security, and the integrity of data provided by preventing the involvement of the middle party overseeing all processes.
Scholars have displayed considerable interest in the platform’s progress, challenges, and development. Various distributed ledger systems possess diversified features more effective in surpassing other platforms.
Different distributed ledger solutions that are used have varying data structures, consensus mechanisms, and fault tolerance that render major differences in cost, performance, latency, and security.
Table of Contents
Introduction to DLT technology
The main reason for implementing DLT is to trust a system that does not have a central authority to rely on. In this system, people are not relatives or friends and are not expected to trust each other.
DLT comprises data structures and functions that are essential in managing them. Each DLT has its data model and process, relying on three technologies: distributed peer-to-peer networks, public key cryptography, and consensus algorithms.
Public key cryptography offers confidentiality and identification to all the systems in the network since no one is trustworthy in a decentralized environment. Every party has a public and private key pair to write the transaction data in the distributed ledger (DL).
Members use their digital identity to punish others for breaching rules governing the items that are under the custody of DL.
A distributed peer-to-peer network is self-organizing and fault-tolerant, which means it lacks specific points of failure, is scalable and efficient and is resistant to a hostile takeover by a member or members of a network.
The proof-of-work consensus mechanism is the foundation of any distributed ledger. It relies on a scenario where none of the participants can trust the other; in this, it makes it possible for all members to be in concurrence with the truth.
Some of the desirable properties of a consensus algorithm are determinism, fairness, security, and speed. It must accommodate Byzantine behavior.
Understanding the blockchain technology
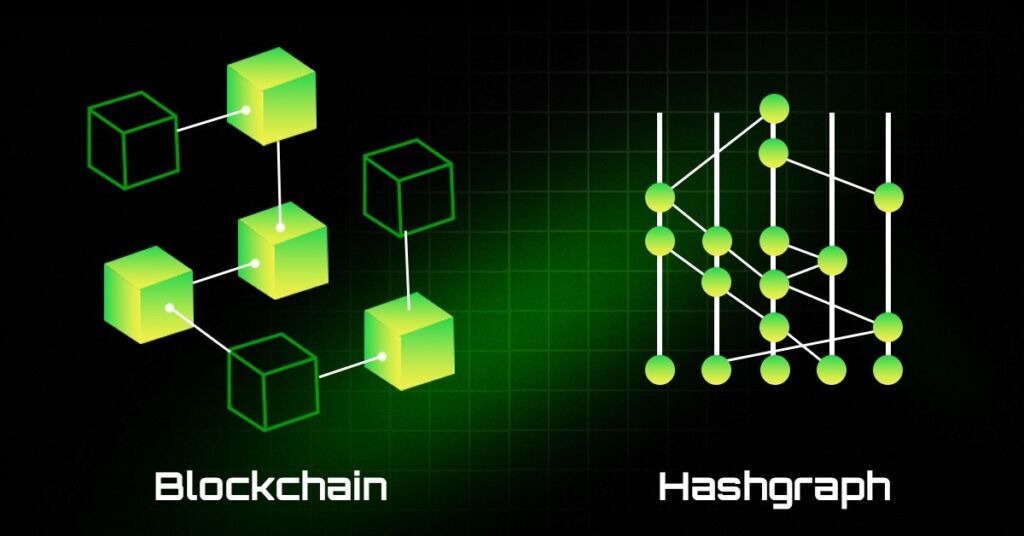
In the blockchain, transactions are recorded in blocks and added sequentially over time; they are also available to all members of the network, modifying a block’s contents is challenging because it breaks the chain, and each block also contains the hash of the previous block.
The components of blockchain are:
- Network member signs information that is related to a transaction digitally. Other participants are also referred to as validators or miners who involve transactions in the blockchain.
- The blockchain ledger stores transactions to all further blocks employing a hash of the prior block like a linked list.
The blocks of the ledger form a blockchain network in a sequence that resembles a chain. Since each block includes transactions, besides the data associated with the previous block. Each transaction creates a new block in the blockchain and connects all the blocks in sequential order.
Blockchain is a decentralized ledger that is managed by multiple nodes that update the chain, hence the blockchain function operates under consensus that is not governed by an individual or an organization, blockchain technology implements various techniques and protocols for block controlling that comprise proof of work and proof of stake.
Features of blockchain technology
Blockchain systems are a favorite and popular solution among different industries and businesses. Many fields are addressed by these technologies. A distributed ledger (dl) is to be offered by blockchain in the hope that all players in the network can affirm that they have the same record.
Smart contracts are a set of rules programmed as logic that can be executed on the blockchain when specific requirements are met. A reward system exists in the blockchain whereby those who add a block to the blockchain are rewarded by members, who mine new blocks in the blockchain are known as miners.
Understanding the Hashgraph technology
Hashgraph was developed by Leemon Baird, who is the founder and CTO of Swirlds, in the year 2016. This platform may work in adversarial settings and supports distributed consensus.
Swirlds is a protocol-type system where only the members who are allowed to join the group are allowed to do so and every member recognizes all the other members.
At an abstract level, a hashgraph can be described as a network structure with columns figuring as the members. Every column has several vertices or nodes. Here, each vertex stands for an event.
Two main actions are taken by a network user: It occurs in two ways:
(i) events are created and submitted and (ii) a network member is randomly selected to gossip all the information or broadcast it. These events contain four categories of information in their data structure:
- The user submits zero or more transactions.
- This category contains the timestamp or creation time of the event.
- The list of all previous events created by the user is revealed.
- The hash of another user’s event that sent the gossip is provided.
The event information is electronically signed by the user and forwarded to respective parties. This shows that the information collected during an event does not largely revolve around use for purchases only.
Members, in this case, can be useful in demonstrating the flow of transactions by using two different hashes. This information is then used by the hashgraph to generate a directed acyclic graph or a DAG of events.
Feature of hashgraph
- Fairness: To ensure that there is a proper flow of the events all the events are done with a time stamp.
- Fast: It is due to the gossip-about-gossip protocol through which the transaction can go high throughput per second. This approach provides immediate event dissemination in a network by selecting a member at random to broadcast messages without considering any condition or area.
The consensus timestamp is not gauged by the heads or by a majority of the participants such that in a scenario where three-fourth of the participants voted to choose a certain time and it will not be followed it will not be followed.
- Virtual voting: Building up a DAG of the events, everyone has the full history of transactions with no need to perform any more intermediate computations. No force would compel a member to transfer his voters to another member to vote.
It is quite easy to predict how a node would vote if one has to build a hashgraph DAG as all the nodes have full details of the other nodes. It helps to determine when one is to make a particular transaction.
This information helps in determining the sequential order of the transactions. Therefore, there is an individual consensus on the order of the events within a node due to DAG creation on each of them.
• Extremely efficient:
Any DAG that is built is used by all of the events. Integrated applications pass only the specific data required for the transaction across the network and these are passed in moderation. No votes are exchanged.
Comparison Blockchain vs. Hashgraph
| Criteria | Blockchain | Hash graph |
| Architecture | Linked list | DAG |
| Transaction | Block in a group | Events in group |
| Consensus | Proof of work | Virtual Voting |
| Latency | In minutes | In seconds |
| Throughput | 5-20 tps | 1 lac tps |
| Security | High | High |
| Privacy | Low | Low |
Conclusion
Distributed ledger technologies can be used in different spheres successfully. It poses a highly significant risk to the current intermediary services inherent in the current financial system like banks which will relay their service on charges.
The following section demonstrates and reviews selected DLTs based on the criteria elaborated in the section above.
When all the hype around Bitcoin and Ethereum started, the latter was among the forerunners who provided the main values, such as decentralization, trust, security, and low cost of operating costs.
