Table of Contents
What if all that we believed was safe—our bank transfer, confidential messages, and national secrets—can be wiped out instantly because of quantum computers? The digital era, fueled by classical cryptography, is on the verge of being revolutionized. Because quantum computing is growing exponentially, traditional cryptographic techniques are failing. The solution to this impending threat is a breakthrough technology in the form of Post Quantum Encryption—a quantum-proof method that is capable of deflecting even the most aggressive quantum attacks.
This emerging technology is reshaping the future of cybersecurity by preparing for a world where quantum computers can crack current encryption standards in seconds. In this article, we’ll discover what Post-Quantum Encryption is, why it is relevant, how it works, and how it is changing the future of unbreakable digital security.
Rethinking Digital Safety: The Post-Quantum Landscape
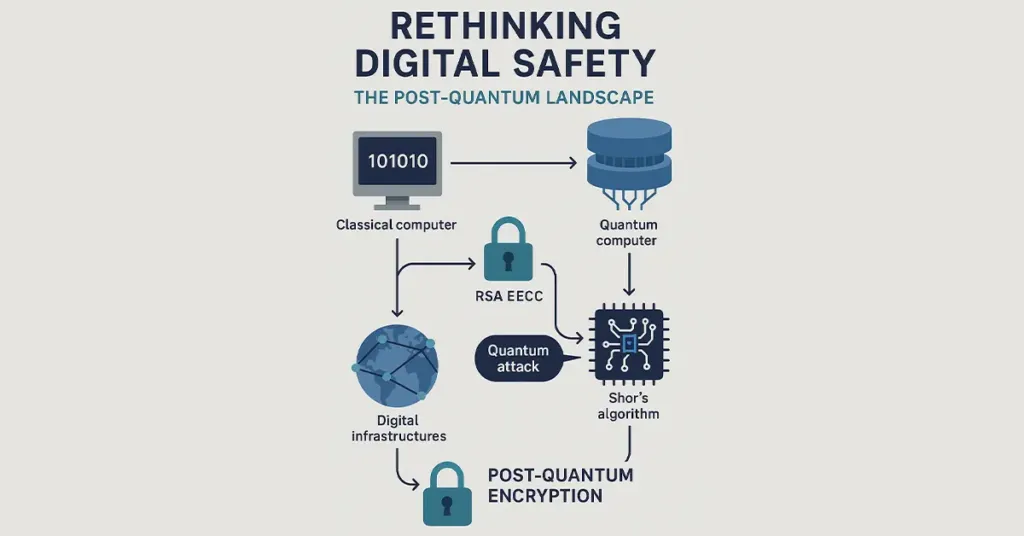
Quantum computers apply the principles of quantum mechanics for calculations that surpasses the limits of functionality of classical computers.. The foundations of today’s encryption, RSA and ECC, can be hacked using algorithms like Shor’s algorithm literally in a split second across classical computers. That is with the coming of age of quantum computing, current encryption will become obsolete.
Post-Quantum Encryption refers to cryptographic schemes that are quantum- and classical computer-resistant. It is not quantum-mechanical but rather mathematical problems believed to be hard for both machine classes. Using these crypto techniques now, we can start to protect digital infrastructures well before quantum attacks are mainstream.
AI and Data Protection: A New Methodology for Future Security
Redefining Our Strategy for AI-Safe Systems
In order to have a safe and ethical future where artificial intelligence (AI) is both ethical and not at the cost of human data, we need to redefine our digital defenses. Data protection is the linchpin—not merely for privacy, but to ensure that AI doesn’t become cataclysmically autonomous.
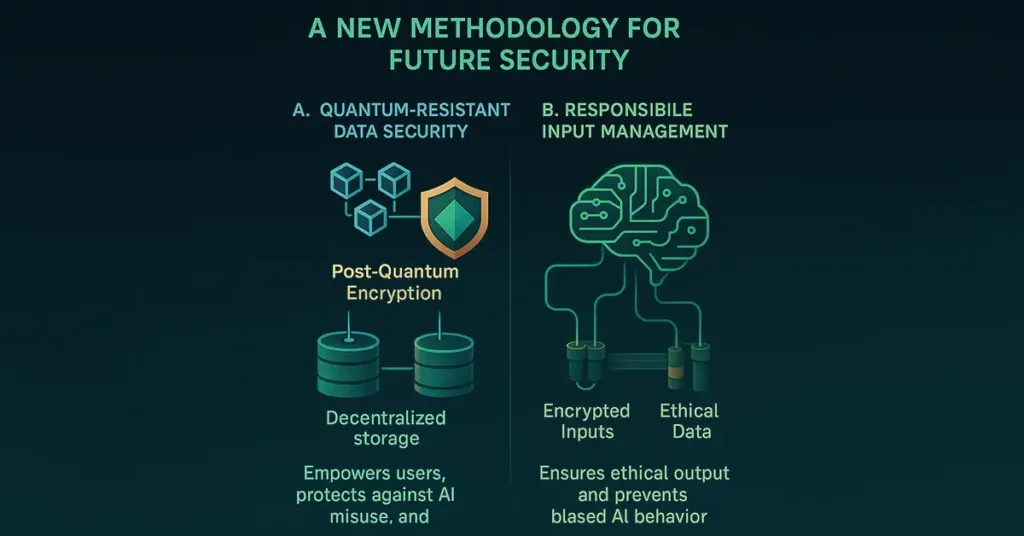
A. Quantum-Resistant Data Security
The highest priority is to create secure, decentralized models for encrypted data storage. Post-Quantum Encryption has a crucial role to play here. In contrast to conventional models, post-quantum cryptographic models are quantum-proof against decryption attacks. For example, blockchain-based projects such as NCOG Earth Chain have already started deploying decentralized storage systems driven by post-quantum algorithms. This empowers users with control over their data and excludes the possibility of centralized attacks or AI manipulation.
Mass-scale adoption of post-quantum encryption protocols will yield a platform in which AI is regulated, managed, and does not manipulate human information.
B. Responsible Input Management
The AI effectiveness level exists only concerning what is being put into it. Flawed or ill-intentioned input will yield biased, offending, or even threatening output. This requires proactive work to sustain training data integrity. Promoting ethical input procurement, enforcing labeling procedures, and employing encrypted inputs through Post-Quantum Encryption ensures AI as a beneficial resource, not a disruptive force.
By keeping our sights on safe, quantum-resistant streams of data, we effectively provide a firewall against bad AI’s ill-behavior, affirming human agency for all online engagements.
How Post-Quantum Encryption Works
Post-Quantum Encryption is based on hard math problems like lattice-based cryptography, multivariate polynomial equations, and hash-based signatures. They are quantum and classical attack vector-proofed. As opposed to RSA or ECC, which quantum computers with known algorithms can easily break, these post-quantum options currently have no effective solution on any paradigm of computing.
Strong contenders are-
- NTRU and Kyber (Lattice-based systems)
- SPHINCS+ (Hash-based signatures)
- Rainbow (Multivariate-based cryptography)
These algorithms are currently being tested by organizations such as NIST, which is actively working to standardize post-quantum algorithms by 2024 and later. The goal is to provide cryptographic solutions that can replace vulnerable systems without compromising speed, scalability, and long-term feasibility.
Real-World Applications of Post-Quantum Encryption
Post-Quantum Encryption is no longer a hypothetical protection—it’s already in use across industries and systems-
- Quantum-resistant keys are being used by banks to secure transactions.
- Blockchain platforms are implementing post-quantum signatures to future-proof their protocols.
- Government agencies are investing in migration strategies to protect classified data.
- Cloud service providers are trying hybrid models that use a combination of legacy and post-quantum encryption algorithms.
FAQs
What is Post-Quantum Encryption?
It refers to a suite of Crypto protocols safe from classical attacks and quantum computer attacks. It supersedes traditional forms of encryption, which can be broken by a quantum computer.
Why is Post-Quantum Encryption necessary?
Quantum computers will have the ability to break commonly employed encryption schemes such as RSA and ECC shortly. To keep secret data confidential, there is a need to seek out quantum-proof systems that resist such sophisticated attacks.
How is Post-Quantum Encryption different from classical encryption?
Traditional cryptography relies on issues such as an integer factorization or the discrete logarithm that are trivial to quantum computers to solve. Unlike them, new encryption methods use complicated mathematical objects that are still hard for quantum machines to access.
When will quantum computers be able to break current encryption?
Quantum machines are difficult to estimate, but most professionals believe that in 10–20 years, they will be small enough and stable enough to be a serious threat. Preparing now with new encryption methods is a proactive step to prevent future breaches.
Which sectors are most at risk?
Finance, defense, health care, and government are a few sectors dealing with sensitive data that, if decrypted, would be extremely valuable. These sectors are taking utmost seriousness in implementing newer methods of encryption, which can help reduce the chances of having a future breach.
Can AI reap benefits from Post-Quantum Encryption?
Yes. By encrypting data inputs and storage using post-quantum cryptographic techniques, AI systems can be used more securely and ethically, minimizing the likelihood of exploitation or manipulation and ensuring data processed integrity.
Is blockchain compatible with Quantum Encryption?
Yes. Various blockchain networks are testing post-quantum cryptographic layers to make them viable in the long term. These include quantum-resistant signatures and hash protocols.
What is NCOG, and what does it have to do with Post-Quantum Encryption?
NCOG is a blockchain initiative that utilizes decentralized, encrypted data storage for identity and ownership protection. It offers a platform for the protection of personal data and digital assets from evolving threats posed by quantum computing and AI-based technologies.
How will Post Quantum Encryption influence cloud computing?
Cloud computing based on legacy cryptography can be vulnerable to quantum decryption. Switching to next-generation encryption processes ensures user data is secure and private, even in distributed or shared systems, protecting it from the new dangers of ultra-powerful quantum computing platforms.
How do people prepare?
To gear up for the quantum future, one should prefer using end-to-end encryption platforms, never conduct sensitive information transactions over public Wi-Fi, and remain updated with post-quantum encryption advances. Additionally, one can choose those services that embrace such future-proof security standards to protect their virtual assets.
Are there any disadvantages of Post Quantum Encryption?
Post-quantum algorithms trade off sometimes being more computationally intensive, and in some cases, having larger key sizes. Such trade-offs are generally acceptable considering the extra degree of security they offer.
How does Post Quantum Encryption safeguard against identity theft?
By rendering decryption effectively impossible—even to quantum computers—new generation encryption techniques safeguard personal data, drastically lowering the risk of identity theft and enhancing security from emerging cyber threats.
Explain the role of NIST in standardizing these algorithms?
NIST is leading the world’s initiative to test and standardize the best post-quantum encryption methods in town. These will be international cybersecurity standards in the future.
Can post-quantum computers break Quantum Encryption?
Up to now, no quantum algorithm efficient to solve the challenges used in Post Quantum Encryption exists, and thus it’s one of the best existing defenses.
Is Post Quantum Encryption scalable?
As a result of recent advances, most post-quantum algorithms are scalable, efficient, and can be embedded in mobile apps, cloud infrastructure, and IoT devices.
How does it improve AI data integrity?
By encrypting system inputs and training data with Post Quantum Encryption, we provide immunity against tampering and allow AI systems to operate as designed, ensuring safety and fairness.
What is a hybrid encryption model?
A hybrid model leverages classical and Quantum Encryption to ensure backward compatibility in moving towards future-proofing security.
Will websites be required to update SSL/TLS for post-quantum security?
Yes. TLS protocols shall have to include post-quantum key exchange algorithms to ensure continued security. This will have to be done for all HTTPS connections henceforth.
How can developers begin incorporating Post Quantum Encryption?
Post-quantum algorithm-friendly open-source libraries are at hand for developers to keep themselves abreast of NIST guidelines and get their systems ready well in advance.
Is Post Quantum Encryption the silver bullet?
Not a silver bullet by itself, by any means, Post-Quantum Encryption is one of the most urgently required tools to combat quantum-age cyber attacks. It is the corner-stone together with decentralized data platforms and sound practices for AI on which digital security of the future depends.
Conclusion
Quantum computing is inevitable, as is the reversal of it. With Quantum Encryption, we’re building a digitally unbreakable system that resists not only cyberattacks of the day, but the ones of tomorrow too. By integrating these high-level encryption mechanisms with smart AI ethics and data ownership decentralization, we’re not only protecting information, our digital identity, freedom, and future.
References-
(Rob Clyde, post-quantum cryptography)
(David O’Berry, Preparing for the Future of Post-Quantum Cryptography)
(RocketMe Up Cybersecurity, Post-Quantum Cryptography — Preparing for a Quantum-Resistant Future)
