What becomes of encryption today when quantum computers are capable of cracking it? As we race toward a future driven by the next generation of technology, one urgent question hangs over cybersecurity. The solution is to use Post Quantum Security, a new generation of cryptography capable of resisting the brute power of quantum computing.
In a world where sensitive information—from personal identities to national secrets—is increasingly vulnerable, Post Quantum Security is not just an upgrade, but a necessity. This article explores how to future-proof your data and systems against quantum threats.
Understanding the Quantum Threat Landscape
The Birth of Quantum Computing
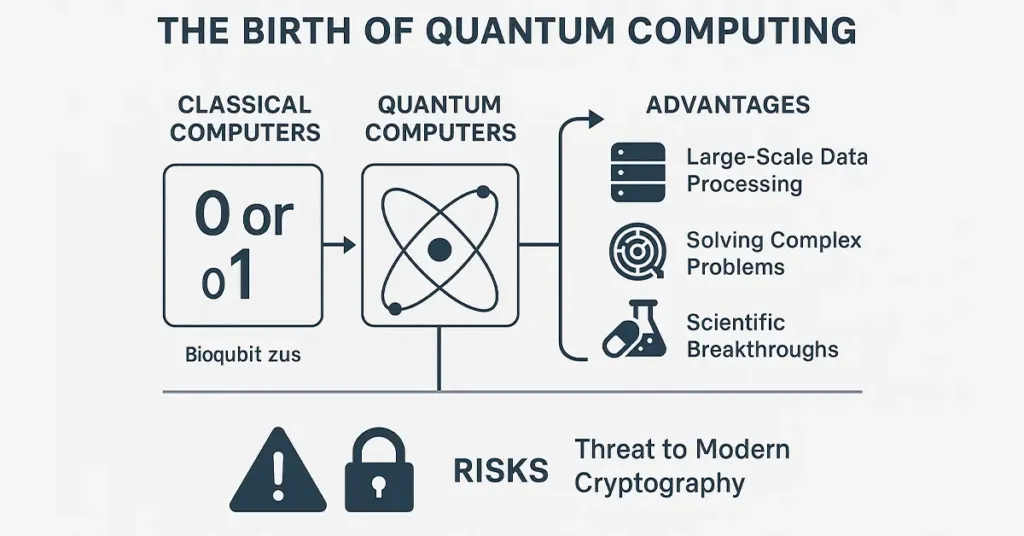
Quantum computing seems to quickly evolve from a new scientific theory into a change- and results-driven technology. Old computers use the binary digit as 0 or 1, whereas quantum computers operate using qubits, which can occupy several states simultaneously owing to superposition and entanglement. As a result, such cutting-edge machines provide an exceptional ability for quick, advanced computations.
Quantum computing excels using its capability of handling large data volumes and solving issues too complicated for existing best classical supercomputers. In particular, quantum computers can effectively address complex logistics tasks, analyze the structure of molecules to invent new medicines, and enhance the approach undertaken in financial forecasting.
But with that potential comes a warning: quantum computing puts modern cryptographic systems at serious risk. The same computational benefits that make quantum computers a breakthrough for scientific research are the ability to compromise classical encryption methods used in our online security.
Implications for Current Cryptography
The dominant modalities of the modern digital infrastructure are based on the use of public key cryptography, and such systems as RSA and ECC are among the most widespread representations that people use. These encryption systems are based on mathematically difficult problems for conventional systems—factorizing huge numbers or solving discrete logarithm problems. These are exactly the sorts of problems a quantum computer is designed to demolish with impunity using expert algorithms.
Shor’s Algorithm, created in 1994, is likely the most famous quantum algorithm that targets RSA and ECC directly. It can factor big numbers exponentially quicker than the best-known classical algorithms. When quantum computers are ready—usually called “quantum supremacy”—they will be able to decrypt secure communications, financial transactions, and private information that are now thought to be secure.
Another significant algorithm, Grover’s Algorithm, doesn’t shatter symmetric crypto systems but narrows down their security levels significantly. It indeed cuts a symmetric key’s bits in half, so 256-bit keys would provide only 128-bit security in the quantum age. Less devastating than Shor’s impact on asymmetric crypto, though, Grover’s Algorithm does mean a reconsideration of the dominant symmetric encryption algorithms.
This new threat brings to the forefront the need for post quantum security solutions in an immediate manner. Unlike conventional cryptographic practices, post quantum security is about designing and deploying algorithms that are secure even when quantum computing resources are available. These algorithms are based on challenging mathematical problems for which quantum computers are not yet known to solve efficiently.
The Urgency for Transition
Post quantum security is not a theoretical concept; it’s an urgent, real-life issue. RSA- or ECC-breaking large-scale quantum computers don’t exist yet, but breakthroughs are on the move. The collaborative efforts of governments, corporations, and research bodies across the globe to create quantum technology imply that these machines will soon become real.
There is a dire need to secure the digital infrastructure of organizations, for when quantum technology is available. Transitioning to post quantum security protocols is difficult and time-consuming, not only swapping cryptographic algorithms but also rewriting software, hardware, and communication protocols. Waiting for fully functional quantum computers may expose systems and data to attacks.
Further, hacked encrypted data today can be stored and decoded at a later date after computers develop the capability—the “harvest now, decrypt later” attack. As a countermeasure post quantum security ensures valuable information is safeguarded both today and in the foreseeable future.
The U.S. National Institute of Standards and Technology (NIST) has already started standardizing quantum-resistant algorithms with its Post-Quantum Cryptography Standardization Project. Organizations can standardize their security approach with international best practices for post quantum security using NIST-recommended solutions.
What Is Post Quantum Security?
Post Quantum Security is a term that is used to refer to cryptographic methods that are resistant to attacks carried out by entities that can run large quantum computers. Besides, this category includes the quantum-resistant hash algorithms, encryption algorithms, and digital signature algorithms. These systems are being standardized by efforts such as NIST’s Post-Quantum Cryptography Project.
Embracing Post Quantum Security guarantees that long-lived sensitive information, such as medical records or financial contracts, is still protected even when intercepted today and decrypted in the future quantum world.
ncog.earth incorporates Post Quantum Security into its core blockchain protocol. It provides data security for decades in a post-quantum secure environment.
Core Principles of Post Quantum Security
Below are the fundamental principles that constitute this new field and how they interact with each other to protect digital property during the era of quantum computing.
1. Quantum-Resistant Algorithms
Post quantum security is centered around quantum-resistant algorithms, which are designed to stand up to attacks both from traditional attack methodologies as well as attacks performed with a quantum computer. These algorithms don’t depend on the weak assumptions of the classical encryption methods like RSA or ECC, which can be attacked and broken by quantum algorithms like Shor. Post quantum security instead depends on mathematical problems with cryptographically amicable properties that are difficult for an efficient quantum computer to solve.
Among the most promising quantum-resistant solutions are-
- Lattice-based cryptography: Lattice-based cryptosystems rely on the computational subtlety of such problems as the Shortest Vector Problem (SVP) and the Learning With Errors (LWE) problem. They are classical and quantum resistant and thus well positioned to protect encryption, digital signatures, and key exchanges.
- Hash-based cryptography: Founded on extensively studied hash functions, this method effectively generates secure digital signatures. Because hash functions are one-way functions, they are extremely secure even against quantum attackers.
- Code-based cryptography: Founded on error-correcting codes, this method has stood the test of time for more than four decades. It is strong, well-established, and extremely efficient for encryption and digital signatures in a post quantum security scenario.
- Multivariate polynomial cryptography: The hardness of these problems is essentially dependent on the intricacies of solving multivariate quadratic systems of equations, which are intractable for quantum and classical systems.
Deployment and selection of these algorithms are being standardized by bodies such as NIST, which is finalizing a suite of post-quantum cryptographic standards for ease of global implementation of post quantum security protocols.
2. Forward Secrecy
Forward secrecy is yet another significant post quantum security parameter. In the conventional crypto paradigm, it might be possible that breaking a private key today can expose attackers to decrypted communications in the past and future, and it is highly risky if, in a quantum paradigm where harvested encrypted data from today can be broken using quantum computers in the future.
Post quantum security addresses this issue by guaranteeing that even when an encryption key is finally breached, past messages cannot be decoded after the fact. The method is to repeatedly generate ephemeral keys that don’t survive and aren’t easily linked up with each other. Forward secrecy is significant not just for private individuals but for protecting business networks, government files, and money networks as well.
Essentially, forward secrecy reconfigures the way we approach long-term data secrecy, particularly considering the danger represented by “harvest now, decrypt later” attacks facilitated by quantum advancements. In post quantum security, it’s a solid pillar of real future-proofing.
3. Hybrid Cryptographic Models
With the indefinite time frame of quantum progress, most organizations are taking a hybrid approach that brings together classical and post-quantum-resistant cryptography. The cryptographic models are created to fill the security gap during the transition phase when the existing traditional algorithms exist side by side with the post quantum security algorithms.
In a hybrid method, two sets of algorithms are run in parallel. One set offers backwards compatibility with current infrastructures, and the other offers immunity to future quantum attacks. As a simple example, an end-to-end communication channel could employ RSA in conjunction with a lattice-based encryption scheme at the same time. This means that even if the classical part is compromised in the future, the post quantum security layer still protects the underlying data.
This method has some advantages-
- Gradual roll-out: Businesses can deploy systems gradually without affecting current services.
- Redundancy: Having several levels of encryption offers a backup in case one algorithm is compromised.
- Testing ground: Testing the deployment of quantum-resilient tools identifies real-world problems and solutions before mass deployment.
Hybrid deployments are not long-term, but they are essential stepping stones. With increasing trust and confidence in post quantum security technology, hybrid deployments will ultimately make way for fully quantum-resistant architectures.
Why Businesses Must Act Now
In the unfolding digital age, while cyberattacks increase in scale and sophistication, quantum computing’s emergence is at once a dazzling technological advancement and an intrinsic cybersecurity challenge. To companies—particularly those holding sensitive customer data or conducting business in highly regulated industries—the time to prepare is not in the future but today. Post-quantum security is no longer an idealistic aspiration but rather a concrete reality. Forward-thinking companies need to take action today to ensure that they will be able to withstand future cryptographic shocks.
Quantum Threats Are Nearer Than They Seem
The power of quantum computers is that they can use superposition and entanglement to exceed classical machines in certain forms of mathematical operations. The possible advantages that such technology could offer to drug discovery and logistics, as well as machine learning, are substantial, but this danger also undermines the encryption protection that enshrines secure digital communication, financial systems, medical records, and contracts.
Algorithms such as RSA and ECC, the basis of modern public-key cryptography, could be made obsolete by quantum algorithms such as Shor’s. In practical terms, what that would mean is to make information currently encrypted under these systems decrypted within seconds if there existed a sufficiently large quantum computer. The potential effect would be disastrous to companies experiencing huge-scale data breaches, litigations, and erosion of customer confidence.
That’s why post quantum security must be implemented far ahead of the wholesale arrival of quantum computing. Companies that delay are not only taking a risk—they’re deliberately putting their businesses, data, and reputations in long-term jeopardy.
Data Longevity Brings the Risk into the Present
One of the least considered measures of quantum risk is data longevity concern. Whereas real-time data spoils at a fast pace, some forms of data—medical history, legal papers, government agreements, and intellectual property—are priceless for decades or years. If today a cyberattacker got hold of encrypted information, they would be unable to decipher it. But with the advent of quantum power, the same information can be accessed in the foreseeable future. The label is also applicable when talking about attacks referred to as “harvest now, decrypt later”.
On this front, post quantum security plays a twofold role: it safeguards against the threat at hand, but also against potential attempts to decrypt in the future. For businesses tasked with securing data over the long term—insurance providers, banks, and law firms, for example—it is critical that it is pre-emptive. Delaying the implementation of quantum-resistant practices creates a bombshell situation where encrypted files stored could be cracked open at any moment.
Consumer confidence is perhaps the most precious asset of the online marketplace. With high-profile breaches becoming the norm, customers are growing more attuned to where their information lives and how it is secured. Companies that act early to publish quantum security standards communicate that they are serious about leading-edge data protection and customer privacy. This method contributes to the creation and preservation of a reliable brand and earns the loyalty of the clients.
Additionally, regulatory landscapes are changing. Global data privacy legislation like the GDPR, HIPAA, and CCPA demands secure data security procedures, and compliance systems will shortly be following close behind in counteracting quantum-age attacks. Adopting post quantum security today allows organizations to protect themselves against future compliance mandates and sidestep the prohibitively cost-intensive exercise of currency flows.
Smooth Transition Through Strategic Planning
Post quantum migration is not a flip-of-the-switch transition—it requires thoughtful planning, testing, and staged deployment. Businesses must assess their existing cryptographic infrastructure, identify vulnerable endpoints, and decide which quantum-resistant algorithms will best meet their operational needs.
Fortunately, most businesses are not beginning from the ground up. Hybrid crypto designs—blends of conventional and quantum-resistant solutions—permit phased and secure adoption. Post quantum security is viable through hybrid approaches that support organizations in adopting post quantum security without sacrificing current system performance or compatibility. Phase by phase is the way, causing as little disruption as possible while providing security for important information at each stage.
They also must spend on training and awareness programs. Decision-makers, developers, and cybersecurity staff must be made aware of the effects of quantum risk and the pragmatic actions that go into minimizing it. Post quantum security incorporated into cybersecurity roadmaps now will have companies not lag when the quantum era is in full force.
Building Quantum-Resilient Ecosystems
The truth is, cybersecurity is not an isolated practice. A majority of businesses employ third-party suppliers, cloud computing providers, and digital platforms that touch or have access to sensitive information. Having a secure digital environment is a matter of discussing post quantum security with partners and suppliers.
Leading organizations are now starting to measure their supply chains and expect quantum-readiness from their partners. Organizations can minimize systemic vulnerabilities and foster increased collective resilience by establishing post-quantum security as an expectation within ecosystems.
Integrating Post Quantum Security into Your Infrastructure
With continued advances in quantum computing, the danger that it poses to classical cryptographic schemes is more dire. Companies and enterprises cannot afford to wait. There is a need for a transparent and systematic adoption of post quantum security protocols into existing IT infrastructures so that data confidentiality, integrity, and availability are preserved under quantum computing. This has to be done with a strategic roadmap of action covering technology and operations transformation across the digital landscape.
For this transition to be made possible, organizations can utilize a multi-step process that will establish quantum resilience without disrupting essential services. Below, we outline the four main steps of incorporating post-quantum security in your infrastructure.
Audit Your Current Cryptographic Inventory
Before any change is implemented by companies, they must start by defining the scope and utilization of current cryptographic assets. Any effective post quantum security project is based on a thorough cryptographic inventory. This process entails determining where and how cryptographic algorithms are utilized—on SSL/TLS certificates, database encryption, secure email, authentication protocols, digital signatures, API gateways, mobile applications, VPNs, and IoT devices.
This audit must encompass-
- Encryption Algorithms Used: Assess if systems are using RSA, ECC, or other vulnerable algorithm-based encryption.
- Key Sizes and Expiration Policies: Document existing key sizes and assess how often they are being replaced.
- Cryptographic Libraries and APIs: Check for dependencies and assess compatibility with quantum-resistant alternatives.
- Certificate Authorities and Issuance Policies: Examine methods of distributing, retaining, and withdrawing digital certificates.
When such data is analyzed, it is possible to identify weak points and establish priorities for strategic transition to post-quantum security. Notably, the process helps organizations to review the data lifecycle and determine long-term sensitive data that needs to be secured today against tomorrow’s quantum decryption power.
Select Quantum-Resistant Algorithms
After identifying your cryptographic footprint, the next step is to select quantum-resistant alternatives. NIST has worked with others to initiate multi-year standardization efforts that will evaluate and promote post-quantum cryptography algorithm recommendations. These algorithms are designed so that they can resist attack by both classical and quantum computers and include key encapsulation processes and digital signature protocols.
Among the most promising contributions to come out of the NIST project are-
- CRYSTALS-Kyber (for public-key cryptography and KEM)
- CRYSTALS-Dilithium (for digital signatures)
- FALCON and SPHINCS+ (signature schemes with performance profiles of differing types)
In choosing algorithms, implementations must consider performance, resource efficiency, complexity to implement, and the extent to which the solution they choose fits their infrastructure. For instance, IoT devices that have little power may need lightweight algorithms, but high performance servers are more than capable of handling complex computing activities.
Selection of the best algorithms is immensely important for effective post quantum security integration. Future-proofing should also be a consideration for security teams as quantum-resistant cryptography develops. Modular architecture solutions for cryptography allow for a seamless switch or upgrade of algorithms as new standards become available.
Use Hybrid Cryptographic Systems
It is not necessary to move away from classical to quantum-resistant cryptography completely. One of the most recommended practices while transitioning to post quantum security is the use of hybrid cryptographic systems. These use current (classical) cryptographic algorithms and couple them with quantum-safe algorithms to provide a multi-layered defense.
In a hybrid system, data is encrypted with both RSA (or ECC) and a quantum-resistant algorithm. It makes the system both backward compatible as well as future-proof against attacks based on quantum. Although quantum computers are unable to break today’s classical encryption now, hybrid encryption protects the data from being exposed in the future, most beneficial for long-shelf-life sensitive data.
Hybrid deployments also enable companies to pilot the in-the-wild usage of post-quantum-safe algorithms without removing trusted current defenses. Phase-in of post quantum security in this manner prevents service disruption, lowers operational risk, and enables incremental testing and tightening.
Key libraries and frameworks increasingly start to include hybrid support. For example-
- OpenSSL (with quantum-safe branches)
- Cloudflare and Amazon Web Services, which have begun to experiment with post-quantum TLS deployments
- Mozilla and Google, pioneering early hybrid deployments in their browsers
These initial hybrid adoption attempts show the growing traction for post-quantum security and offer in-the-wild blueprints for companies willing to make the transition.
Upgrade Key Management Systems (KMS)
The key to the efficiency of encryption lies entirely in the responsible use of its keys. Infrastructures that are quantum-resilient need updates to legacy Key Management Systems (KMS) to accommodate the special needs of post quantum security. This involves reconsidering key generation, storage, transport, and rotation.
Key changes are-
- Quantum-Safe Key Generation: Conditionally preconditioning random number generators (RNGs) employed in key generation to be quantum-inference or side-channel resilient.
- Larger Key Sizes: Larger keys and signatures are needed for some quantum-resistant algorithms, which could affect memory storage and transmission overhead.
- Metadata and Expiration: New KMS needs to manage algorithm metadata, key expiration according to risk assessments, and post-quantum certificate format support.
- Hardware Security Module (HSM) Integration: Most organizations use HSMs to securely store private keys. Vendors need to make their HSM offerings quantum-safe algorithm-compatible.
- Secure Key Exchange Protocols: These will have to be adapted to employ KEMs that are quantum attack-resistant.
Key Technologies Supporting Post Quantum Security
With the world shifting towards quantum-age computers, the old encryption techniques like RSA and ECC (Elliptic Curve Cryptography) are being put on the back burner. Quantum computers, when they come into existence, can break all but a handful of the cryptographic constructs that have ruled secure communication up to this day. The result is the development of post quantum security, a category of new, innovative encryption strategies for resisting attacks based on future quantum computer powers.
Some promising cryptographic techniques are on the rise to support post quantum security, and among them, lattice-based cryptography, hash-based signatures, and code-based encryption are the top choices. They not only resist quantum attacks but also serve as a bridge between the existing cryptographic era and the quantum-safe era. In this article, we will discuss these new key technologies in detail.
Lattice-Based Cryptography
Lattice-based cryptography is presently among the most developed and controversial forms of post quantum security protocols. Essentially, lattice-based cryptography relies on the mathematical object called a lattice—a collection of points extending out in many directions indefinitely. These form the basis for sophisticated number theory and geometry problems intractable even given the capability of a quantum computer to process.
Lattice-based cryptosystems use the difficulty of certain lattice problems, e.g., the Shortest Vector Problem (SVP) and the Learning With Errors (LWE) problem. These are so computationally expensive that they would take unmanageable amounts of computational power even for a quantum computer, hence, lattice-based schemes are among the strongest post-quantum candidates.
The most studied lattice-based algorithms are-
- Kyber: A KEM chosen by NIST as a candidate for post-quantum cryptographic standardization. Kyber is specifically known to have very strong security guarantees and to be efficient, and is thus especially well-placed to be implemented in hybrid encryption systems as well as in public-key encryption.
- NTRU: A lattice-based public key crypto scheme. NTRU has proved itself to be a good encryption/decryption system, thus, it is fit for several purposes, ranging from secure messaging to digital signatures.
Lattice-based schemes possess several benefits that render them a strong building block for post quantum security. Mainly, they are perceived as secure from a quantum and classical point of view since quantum computers are not well-suited to work with lattice problems. Another benefit is that the support of small key sizes and the ability to operate within a broad spectrum of computing platforms characterize the lattice-based cryptography. The development of quantum computing is going to reveal the relevance of lattice-based cryptography to critical infrastructure and communications systems protection.
Hash-Based Signatures
Hash-based signatures are another vital solution for securing our systems from post-quantum threats. Those cryptographic methods are most precious when computational power is scarce, e.g., in IoT and other lightweight devices, are hash-based signatures. They provide an efficient yet effective means of asserting data authenticity and integrity without depending on high-cost number-theoretic abstractions such as RSA or ECC.
The Hash-based signature systems, for example, “Hash” or “digest,” do so based on a cryptographic hash function that provides an output size that is predefined irrespective of the input message. In the case of hash functions, examples usually illustrate the property of one-wayness and collision-resistance – i.e., finding back the original input out of its hash or getting equal output out of different inputs is practically impossible. For hash signature schemes, the signing function must begin with a private key, end with a public key, and verify the signature by using the process of an initial hashing of the message.
A very popular and widely used hash-based signature scheme is the Merkle Signature Scheme (MSS). MSS relies on a Merkle tree, a tree structure consisting of hashes, to sign and display hashes. In a Merkle tree, internal nodes are hashed using their children, each leaf represents a message hash.
Code-Based Encryption
In the existing post quantum security approaches, code-based encryption is the second most important one. While lattice cryptography relies on theories of geometry, code-based cryptography is associated with error-correcting codes, which are applied daily to detect and correct errors as information travels. The transmission data is decoded by these codes, which enrich its field by adding redundancy, thus making it possible to detect and correct errors, if any occur, to may emerge in it. In cryptography, error-correcting codes are used to lay the basis for the construction of secure cryptographic schemes resistant to quantum attacks.
Code-based encryption encrypts codewords that are, in turn, encrypted. The security of the encryption is based on the computationally difficult problem of decoding these codewords without knowing the proper key. This problem is a decoding problem and is quantum-resistant. The hardness of the decoding problem ensures code-based encryption as a potential post-quantum candidate.
Applications of Post Quantum Security Across Industries
Financial Services
The financial services sector is among the earliest to need strong Post Quantum Security. Banks, trading exchanges, and other institutions in the financial sector are highly dependent on encryption to protect sensitive information like account information, transactions, and customer data. But with the emergence of quantum computing, current encryption algorithms such as RSA and ECC (Elliptic Curve Cryptography) will be open to the sheer powers of quantum computers, breaching these walls of cryptography in a period far less than the time needed by current classical computers.
Financial institutions already have protocols for Post Quantum Security to prevent this attack. By using quantum-resistant algorithms, such institutions are future-proofing their systems in a manner that sensitive data will continue to be secure even after the existence of quantum computers. This is by creating and implementing quantum-attack-immune encryption systems like lattice-based cryptography and hash-based signatures. Since the financial services industry handles trillions of dollars worth of transactions daily, the security of such data is central to maintaining trust and integrity within the system.
Healthcare
Healthcare is also an industry where Post Quantum Security is increasingly important. The security of electronic medical records (EMRs), genomic information, and other personal health data (PHI) has always ranked first. But as the healthcare sector continues to go digital, it now has new issues in protecting this very sensitive information. With quantum computing looming, the cryptographic methods used today to secure patient data can become outdated in a matter of years, leaving hospitals and healthcare providers vulnerable to data breaches and privacy infringements.
By utilizing Post Quantum Security, healthcare professionals can ensure electronic data and genomic data security from current and potential future threats due to cyber attacks and quantum computing. All the personal and health data handled by such systems is enormous in volume and has to be secured. The ability of future quantum computers to exploit weaknesses in present encryption could make it possible for hackers to gain access to systems, steal identities, and develop many more dangerous scenarios.
Government and Defense
National security carries the inherent implication of the necessity for secure communication, intelligence gathered through surveillance, and defense of critical infrastructure. Secure encryption becomes a necessity upon which governments and militaries rely to safeguard everything from wartime communications to secret intelligence. With the future threat posed by advanced quantum computers, governments need immediate deployment of new cryptography not vulnerable to quantum attack and safeguarding sensitive government information.
For example, secure communication through military satellites or encrypted digital channels must be safeguarded against future threats through quantum. Apart from this, surveillance data, with precious intelligence, must be highly encrypted to avoid foreign enemies from invading national security. Therefore, quantum-resistant algorithms are essential to safeguard the confidentiality and integrity of communications at all times, during war and peace.
Moreover, energy grids, transportation networks, and emergency services demand that communication is considered safe for it to work. Quantum leak can incapacitate or destroy such facilities, leading to catastrophic effects. Governments are implementing Post Quantum Security to safeguard their information as well as the infrastructure that guarantees the nation’s safety and health.
Defensively, the necessity for secure encryption is also being applied to military logistics, military weapons, and strategic operations. The Post Quantum Security solutions are the regulator to thwart cyber-attacks based on quantum,, while ensuring protection of military operations and the integrity of intelligence collection.
The Role of Standardization Bodies in Post Quantum Security
The shaping of the trajectory of Post Quantum Security is driven by standard-setting bodies such as NIST, ETSI, and ISO. They are central to formulating cryptographic algorithms and protocols that will be impenetrable to quantum computing attacks. They are responsible for developing harmonized, dependable, and interoperable standards for attaining a worldwide migration towards quantum-resistant security systems.
NIST, specifically, has led the way in Post Quantum Security through its Post-Quantum Cryptography Standardization initiative. The project is designed to test and standardize quantum-resistant cryptographic algorithms to protect data in the long term. NIST’s Round 3 candidates for quantum-safe algorithms are Kyber, Dilithium, and Falcon. Kyber is an encryption scheme based on a lattice designed to deliver safe public-key encryption, whereas Dilithium and Falcon are lattice-based signature schemes designed to deliver safe ways of performing digital signatures against quantum decryption attacks.
Benefits of Early Adoption of Post Quantum Security
Improved Long-Term Data Security
The organizations are turning to Post Quantum Security more because of its long-term ability to protect the data. The emergence of quantum computing can crack the encryption processes that stand nowadays, and expose sensitive data to cyber attacks. Data security is at the top of the list in areas like finance, healthcare, and government. Personal data, money data, and government intelligence all become vulnerable to attack if these conventional cryptographic procedures are broken by quantum attacks.
By embracing Post Quantum Security early, organizations and companies can guarantee their data is safe not only today but also in decades to come. Quantum-resistant algorithms are developed to withstand the strength of quantum computers and therefore offer a safe and solid base for safeguarding information. By such foresight, the danger of a data breach is reduced, and sensitive data is made secure for decades to come as quantum computing technology advances.
Enhanced Regulatory Compliance
Regulations’ compliance is essential for any business working with sensitive data. Financial, healthcare, and governmental bodies work under strict regulations to ensure there is protection of personal data. Quantum computing technologies will evolve, and regulatory authorities will be forced to modify the existing protocols concerning data encryption in response to advances in security concerns.
Companies that embrace Post Quantum Security early on are ahead of the curve regarding compliance with future regulations. This is not only to prevent companies from incurring future fines or penalties, but also a sign that companies are making efforts to secure their customers’ and clients’ information. An organization being an early adopter of Post Quantum Security indicates that the company is going out of its way to address regulatory compliance and is ahead of the game as far as changes in cybersecurity go.
Competitive Differentiation
To be a step ahead of the very competitive market, businesses are always looking for ways to stand out from their competitors. The introduction of new technologies, such as Post Quantum Security, will first make an organization a leader in the market with regards to safety and innovation. To keep up with the pace, businesses that develop quantum-resistant encryption before others can not only ensure themselves a leading role, but also guarantee their industry’s data is secured.
Since data security is top of everyone’s mind, an expectation is growing that companies should be taking proactive cybersecurity measures to win customer confidence. Through taking Post Quantum Security, companies can develop an excellent track of reliability and security, which can be a strong selling point for businesses such as in the finance industry or healthcare, where data safety is key.
Enhanced Readiness for Future Technologies
Lastly, adoption of Post Quantum Security early on enables organizations to position themselves more effectively in anticipation of emerging technology. As quantum computing continues to advance, it will give rise to new technologies that are based on the increased capability of quantum systems to calculate. Such new developments can give rise to new threats and issues in fields like artificial intelligence, machine learning, and data processing.
Companies already Post Quantum Security compliant will be well placed to transition to such emerging technologies. Having secured their data against quantum hacking, they will have a foundation that can be used when they venture into new technologies and innovations. Such anticipation makes companies get ahead of the game, hence becoming stronger and more resilient to the speed of change in the future.
AI, Decentralization, and Post Quantum Security
When AI operates on encrypted, decentralized information, its potential to cause harm is curbed considerably. For example, a decentralized AI system cannot impersonate anyone unless they have his/her private information. Additionally, Post Quantum Security ensures that even if AI is given quantum computing resources, its potential remains limited by encrypted walls. Thus, Post Quantum Security serves a dual purpose—ensuring privacy and limiting AI abuse.
Quantum Safe Crypto: Protecting Digital Assets from Quantum Attacks
The term used to refer to algorithms that safeguard data against quantum computer breaches is quantum safe crypto. So easily compromised by the advances of quantum machines, algorithms such as RSA and ECC are a grave risk. It becomes necessary to use cryptographic methods that resist quantum decryption methods. Technologies like lattice-based and hash-based cryptography lead the way here with a highly effective quantum-proof defense. By implementing Quantum Safe Crypto, businesses and individuals can have confidence that their digital assets, communications, and transactions are safeguarded and will not be subject to the swiftly developing abilities of quantum technology.
Post Quantum Encryption: A New Standard for Cybersecurity
Post Quantum Encryption is focused on creating methods of encryption protected from possible threats from potential quantum computing. Unlike traditional encryption, the algorithms rely on mathematical problems that cannot be solved efficiently by quantum computers. RSA and ECC have become a traditional way of encryption, and therefore, the area of risk associated with the development of quantum computing. To ensure confidentiality, integrity, and long-term security of data from quantum attacks, the employment of post Quantum Encryption is imperatively necessary. Organizations need to put these quantum-resistant practices in place to remain ahead of the possible threat from the emergence of quantum computing.
Post Quantum Blockchain: The Evolution of Decentralized Security
Post Quantum Blockchain implements quantum-resistant cryptographic protocols within blockchain to protect decentralized systems from quantum computing attacks. Since quantum computers can potentially break classical cryptographic algorithms, the use of quantum-resistant solutions ensures cryptocurrencies, smart contracts, and other blockchain use cases. Deploying Post Quantum Blockchain systems ensures the security, integrity, and stability of blockchain networks in the course of the improvement of quantum computing. This forward-thinking mindset is what blockchain systems need to be quantum-proof to keep them secure even if quantum technology occurs.
Post Quantum Secured Blockchain: Reinventing Trust in the Quantum Era
Aiming at blockchain security enhancement, Post Quantum Secured Blockchain employs quantum-resistant cryptography that significantly secures networks from future attacks by quantum computers. Development in quantum technology will make classical cryptographic methods vulnerable to attacks, thereby opening doors to hacking of decentralized data and networks. Via quantum-resistant technology, the potential for quantum-hatched vulnerabilities is virtually zero, making blockchain-based transactions and applications secure, stable, and permanent. This is a method that industries based on blockchain need as it offers them long-term immunity against evolving quantum computing attacks.
Strategies for Implementing Post-Quantum Security
Assessment and Planning
The initial step toward the implementation of Post Quantum Security is to evaluate the existing cryptographic infrastructure. Organizations continue to utilize conventional encryption systems that are about to be useless against quantum attacks. Proper analysis of available cryptographic systems and protocols is central in determining the weak areas that will be exploited using quantum technology. At this point, we concentrate on describing the protected data and resources required, as well as identifying the quantum security of existing encryption methods.
Adoption of Quantum-Resistant Algorithms
After the vulnerabilities are discovered, the next task is to implement the quantum-resistant algorithms. These algorithms give quantum computations security, meaning that confidential information will be safe even when quantum computers are introduced. NIST introduced in 2022 a set of post-quantum algorithms that prove resistant to the threat that quantum computing poses. To attain the objectives for Post Quantum Security, existing systems have to use lattice-based cryptography, code-based cryptography, and hash-based signature algorithms.
Training and Awareness
It is not just the technological transition, however, that needs to take place to seamlessly integrate Post Quantum Security. There also needs to be a change of attitude across the company. Perhaps the most effective way to guarantee that quantum-resistant technology is implemented smoothly is by education and awareness. All stakeholders at every level of the organization – from IT personnel to senior executives – should become aware of the dangers that quantum computing poses and the need to implement Post Quantum Security.
Continuous Monitoring and Updates
Like with any security solution, deployment of Post Quantum Security does not conclude with the installation of the systems. Quantum computing is still far from being in use, and the technology development is progressing extremely. Organizations need to keep constant watch over their Post Quantum Security system to monitor latent flaws or threats. Continuous audits and updates of security solutions must be performed to ensure protection as quantum technologies advance.
Conclusion
The arrival of quantum computing is simultaneously a catastrophic risk and an evolutionary opportunity for the digital age. As more efficient quantum computers become available, eventually they might become powerful enough to break the cryptographic foundations that secure today’s information and communications. To prevent such a risk, one must implement Post Quantum Security measures. They involve quantum-resistant algorithms that are quantum computer-resistant, i.e., cannot be broken by quantum computers. By proceeding with quantum-resistant cryptography, organizations can safeguard confidential information, achieve business resilience, and build stakeholder trust. Pre-emptive action makes it possible to be ready ahead of time to minimize future possible attacks and demonstrates a proactive focus on good cybersecurity in the age of quantum.
FAQs
What is Post Quantum Security?
This new variety of cryptography, known as Post Quantum Security, is designed to protect against the previously unheard-of threat of quantum computers. These systems are customized to withstand decryption challenges posed by powerful algorithms, i.e., classical Shor’s and classical Grover’s, able to dismantle classical cryptographic methods. Organizations, when bold to act now, can secure data for a long time in the future and immunize their digital borders against quantum-enabled cyberattacks.
Why is Post Quantum Security important?
As quantum computers become large enough, they might break down RSA, ECC, and DSA encryption processes, making personal messages, financial records, and the secrets of states susceptible. Post Quantum Security becomes necessary because it actively proposes encryption techniques that are capable of withstanding quantum threats and protecting advanced digital systems and data from future risks.
How does quantum computing pose a threat to existing encryption?
Under many such algorithms as Shor’s, quantum computers factorize large integers at exponential speed compared to classical computers, which compromises the RSA and other public key cryptosystems. Similarly, Grover’s algorithm may make brute-force attacks on symmetric encryption twice as fast.
What are some examples of quantum-resistant algorithms?
Quantum – resistant algorithms have been developed to resist attacks from quantum computers. Examples include certain lattice cryptographic methods such as NTRU and Kyber, hash-based signature systems such as SPHINCS+, and code-based systems such as Classic. These are the basic components for guaranteeing the safety of information transfer outside a future period where conventional encryption mechanisms are weak.
How are organizations preparing for quantum threats?
The first step in protecting against quantum attacks should be addressed by organizations that need to evaluate their cryptographic systems, determine possible weaknesses, and examine quantum-resistant algorithms by using quasi-lab environments. Staff education and knowledge programs are also required. A phased strategic approach to Post Quantum Security ensures that valuable information and infrastructure are safeguarded from impending quantum-powered cyberattacks without stopping current-day activities.
Are there Post Quantum Security standards?
Post Quantum Security standards are being designed by the U.S. National Institute of Standards and Technology (NIST). NIST’s standardization is at its third round, and selected algorithms are CRYSTALS-Kyber for encryption, CRYSTALS-Dilithium for digital signatures, and SPHINCS+ as a fall-back hash-based one. The standards will impact global adoption of quantum-resistant cryptography.
Which industries are most exposed to quantum attacks?
Businesses that work in such sectors as finance, healthcare, defense, aviation, and government, because of their operation with critical, sensitive data, are the most exposed to quantum attacks. Cryptography means that with the quantum computers on the market, these industries that are highly sensitive in terms of data and communications can be decrypted through back doors, whereby confidential information is compromised. Post Quantum Security compliance is essential to offer protection against such imminent attacks.
What does Post Quantum Security have to do with blockchain technology?
Post Quantum Security guarantees are essential to secure the blockchain infrastructure from potential quantum attacks. Derivatives of cryptographic hash functions and digital signatures are extensively used in the technology around the blockchain; however, they are all susceptible to weaknesses that are quantum-computing related. Post Quantum Security ensures protection of the integrity of blockchain operation, improves the security of smart contracts, and protects the wallets from impending quantum threats through the use of quantum-resistant cryptographic techniques.
Is Post Quantum Security compatible with existing systems?
Yes, Post Quantum Security can frequently be applied in conjunction with current systems. Hybrid approaches make it possible to employ quantum-resistant algorithms in addition to conventional cryptographic techniques, providing seamless and less painful migration to post-quantum cryptography. It allows organizations to deploy quantum-safe practices gradually without entirely reworking their present infrastructure, and it offers a safe way ahead as quantum technologies continue to progress.
At what point should organizations start implementing Post Quantum Security?
Organizations must start adopting Post Quantum Security from today in an attempt to defend against future quantum attacks. Now, encrypted data can be held and possibly decrypted once quantum ability has been built, a risk known as “harvest now, decrypt later.” Organizations can avoid this threat and be able to protect their sensitive information in the future against the risks that the development of quantum computing will pose by using quantum-resistant cryptography upfront. Peace of mind and future-oriented security are the return on early implementation.
What is a hybrid cryptographic strategy?
A hybrid cryptographic strategy integrates classical encryption techniques and quantum-resistant methods into a single cryptosystem. It keeps systems safe from both classical and quantum attacks in the transition phase as future quantum computing technologies become available. By utilizing a blend of both categories of algorithms, firms will stay backward compatible with current infrastructure and future-proof themselves by protecting information from future quantum attacks.
Explain the difference between quantum computing and classical computing?
Quantum computers are efficient in using entanglement or superposition to compute data at scale, where it is done simultaneously in parallel. The essence of this distinction is that classical computing works in a way of serial processing, solving one challenge at a time, as it progresses. In utilizing this natural difference, quantum computers can solve difficult problems much faster than classical computing machines.
Will symmetric encryption be impacted by quantum computers too?
Yes, quantum computers will affect symmetric encryption, but less so than asymmetric encryption. Because of Grover’s algorithm, it will be much easier for brute-force attacks to gain access to encrypted information, lowering the real-world protection offered by encryption keys by half. AES-256, for instance, which is widely assumed to be extremely secure via classical computation, would no longer be stronger than AES-128 against quantum attacks.
What is the role of NIST in Post Quantum Security?
NIST is actively involved in the design and standardization of post-quantum resistant cryptographic algorithms (Work on Post-Quantum Cryptography Standardization). The initiative is designed to identify and validate algorithms that are resistant to quantum computer attacks. NIST’s chosen algorithms will be used as global standards, influencing the use of secure cryptographic standards worldwide across industries. NIST’s initiative will make cryptographic systems in the future secure and immune to the changing powers of quantum computers.
Is stored encrypted data at risk from quantum computing?
Yes, stored intercepted encrypted data can be put at risk due to the development of quantum computing. When quantum computers reach a certain level of power, they could break into stored information and reveal confidential details. That is a massive risk, and hence the necessity to start transitioning into quantum-resistant cryptographic practices today, even for data that must remain secure for decades ahead. Anticipating and pushing to enhance encryption practices will make stored data safe against new threats using quantum computing.
Are open-source quantum-resistant tools available?
Quantum-resistant open-source software against algorithms has been created. Software libraries such as Open Quantum Safe (OQS), liboqs, and Bouncy Castle PQC offer quantum-resistant cryptography method implementations. These packages of software can easily be modified and integrated into current systems for testing, evaluation, and migration. With open-source applications, companies can start testing and using quantum-safe algorithms in their software, ahead of an effortless switch to secure crypto practices, ahead of the inevitable arrival of quantum computing.
What is a lattice-based cryptographic system?
The underlying principle of lattice-based cryptographic systems is the assumption that LWE and SVP kinds of problems are’ necessarily hard’ to solve computationally. They are hard for both quantum and classical computers to compute in short periods, and lattice-based systems present a very interesting possibility of quantum-resistant cryptography. Because of their high security, these encryption schemes are at the heart of most of the algorithms that have been chosen as finalists in NIST’s search for quantum-safe standards.
How long will it be before quantum computers become a serious threat?
Though the timeline is unclear on when quantum computers will be a threat, among industry professionals, it is widely believed that within a decade or two, there will be quantum computers to break encryption. Others estimate it within an earlier time frame, depending on quantum technology advancements. Because of this uncertainty, organizations must begin preparing now and implement quantum-resistant techniques to provide long-term data security.
Post Quantum Security, is it just for big businesses?
No, it’s not only large corporations that will require quantum-resistant solutions. Small and medium-sized businesses (SMBs) handling sensitive customer information or operating in regulated sectors must make the move to future-proof their infrastructure. Cyber attacks on any business size do happen, and with more advanced quantum computers, SMBs may be susceptible to data breaches or compromise if something is not done. Avoidance of future damage is essential for any business size.
What is “crypto-agility”?
The core concept in crypto-agility implies the ability of systems to rapidly change between cryptography implementations with minimal reengineering requirements. It is vital for security, especially in the presence of a rapid evolution of cryptographic standards that is increasingly perpetuated with quantum computing. Crypto-agility allows organizations to deploy seamlessly improved, quantum-resistant algorithms at ease with their release to ensure long-term data security and minimize disruptions through the integration of newer cryptography techniques into current systems.
What if an organization delays adopting?
Slowly switching over to quantum-resistant processes greatly accelerates the danger of data breaches. The more sophisticated quantum computers become, the more data encrypted with current methods will be susceptible to decryption. Organizations that move forward early will be far more able to protect their sensitive data, getting ahead of dangers and the expense of falling behind when quantum computing is established.
Brief difference between quantum-safe and quantum-resistant?
Although the terms tend to be used interchangeably, “quantum-resistant” would typically discuss algorithms, up to the current level of our knowledge, that can’t be broken by quantum algorithms. “Quantum-safe,” however, would imply a whole strategy involving security practices and also deployment.
Do quantum computers assist cybersecurity as well?
Quantum computers may potentially be beneficial for cybersecurity in terms of being able to identify threats more rapidly, optimize more efficiently, and probe the size of large sets of data at a higher capacity. Their strength to subvert current cryptographic infrastructures is also a real danger in the immediate future. Future potential is extremely high, but shadowed by present danger to secured information.
Are quantum-safe VPNs available?
Some VPN providers have already begun including quantum-resistant key exchange algorithms, such as lattice-based algorithms, in their protocols. These changes are aimed at protecting VPNs against estimated attacks by next-generation quantum computers. As quantum computer technology continues to advance, the implementation of these quantum-resistant technologies will become essential to keeping privacy and data safe in virtual networks.
How do companies train employees for Post Quantum Security?
Organizations will need to train IT and security staff in quantum threat basics, new cryptographic standards, and best practices for implementation. Professional training workshops and certification programs are also on the horizon.
What are some of the challenges of migration to post-quantum-safe systems?
The challenges are interoperability with existing systems, backward compatibility, performance compromises, and large-scale testing. Despite all these, Post Quantum Security pays in the long run at the cost of short-term hurdles.
Is end-to-end encrypted messaging vulnerable to quantum computing?
Quantum computing can compromise end-to-end encrypted communication applications that are dependent on RSA or ECC-based key exchanges. Quantum attacks can breach these encryption systems, exposing the sensitive information communicated over these applications to vulnerability. To maintain future confidentiality, quantum-resistant key exchange protocols need to be deployed, which can protect communications against future quantum attacks.
Are there global initiatives for Post Quantum Security?
Yes, there are many global initiatives towards counteracting quantum threats. Besides NIST in the United States, European, Japanese, and other global organizations are putting enormous efforts into quantum-safe research and global standardization. They are attempting to establish a global quantum resilience paradigm that secures vital infrastructure and confidential data from future quantum computing attacks.
Can cloud services be made quantum-safe?
Yes, larger cloud vendors are already looking at quantum-resistant cryptographic options for the future. Customers need to have their plan for utilizing quantum-resistant technology discussed with their cloud vendors. Be sure to inquire if they provide quantum-safe key management solutions so sensitive data can be kept safe as quantum computers’ capability grows.
What is the role of hardware in quantum resilience?
Trusted platform modules (TPMs) and hardware security modules (HSMs) are critical to render data secure, and whether they must be replaced or upgraded with the ability to support quantum-safe algorithms will be contingent. Hardware is at the core of the entire infrastructure, which safeguards systems from the impending threat of quantum attacks and, therefore, is a priority to implement quantum-resilient security infrastructures.
References-
(Dhiraj Sehgal, Post-Quantum Cryptography (PQC) and Versa: Future-Proofing Enterprise Security Against Quantum Threats)
(RocketMe Up Cybersecurity, Quantum-Safe Networks — Can We Future-Proof Data Security?)
(Xin Qiu, Enhancing Security with Post-Quantum Cryptography: CommScope’s Expertise and Solutions)
(Devoteam, Post-Quantum Security: Is Your Encryption Obsolete?)
(Kyle Johnson, How to prepare for post-quantum computing security)
(Jordan Kenyon, Taylor Brady, 5 Steps for Implementing the New Post-Quantum Cryptography Standards)
(Engin Zeydan; Luis Blanco; Josep Mangues-Bafalluy; Suayb S. Arslan; Yekta Turk, Post-Quantum Blockchain-Based Decentralized Identity Management for Resource Sharing in Open Radio Access Networks)
(Chad Boutin, NIST Releases First 3 Finalized Post-Quantum Encryption Standards)
(Stephanie Susnjara, What is quantum-safe cryptography?)