Table of Contents
Can current encryption meet the quantum future? With the entry of quantum computing, classical encryption techniques are under the immediate threat of compromise. There has come a new age with the post quantum algorithm as a vital solution. Having the capability to shield data from being vulnerable to quantum attacks, this fascinating technology promises digital security for the future decades. Different from classic crypto schemes, such algorithms resist even sophisticated quantum attacks. But how do they work, and why are they important? In this article, we’ll explore how post-quantum algorithms are reshaping the cybersecurity landscape—and what it means for the future of encryption.
What is a Post Quantum Algorithm?
A post quantum algorithm is an encryption technique implemented to secure sensitive information from the vast processing power of quantum computers. In contrast to the classic encryption method, which can be cracked using the help of algorithms like Shor’s by quantum computers, this new method takes advantage of maths problems that are difficult for both quantum and classical systems to calculate. Quantum computers employ qubits to process information at new rates, endangering the current state of encryption, such as RSA or ECC.
To counter this, post-quantum solutions employ methods such as lattice-based encryption, code-based cryptography, and hash-based signatures. These are long-term security frameworks that keep data safe, even when there are vast numbers of quantum computers available for cryptographic algorithms.
Why We Need Post Quantum Algorithms Today
Although quantum computers are not yet available, post-quantum implementation of the algorithms in the initial stages is unavoidable. Encryption is not for today—it’s for tomorrow’s data too. A cyberthief will tap encrypted data today and crack it when there’s quantum technology in the future.
The application of a post quantum algorithm nowadays assures long-term secure information protection. Government agencies, banks, and medical providers are already transitioning to quantum-resistant systems.
Types of Post Quantum Algorithms
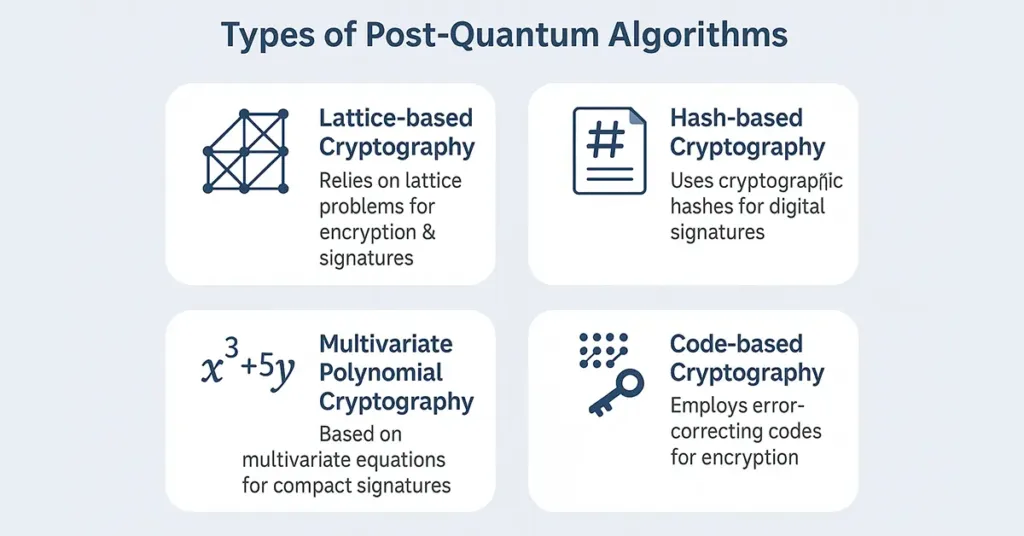
There are various kinds of post quantum algorithms, and each one has special strengths-
- Lattice-based Cryptography: Lattice-based cryptography holds most hope. It relies on lattice problems upon which to build security that even a highly capable quantum computer possesses no way of solving quickly. They do digital signatures and encryption, and are relatively fast. They are quite general, hence are in line for standardization.
- Hash-based Cryptography: Hash-based cryptography is primarily digital signature-based. They enjoy the security of traditional cryptographic hash functions and are safe against known quantum attacks. Very secure and grown-up, but generally not employed for encryption due to their size and slow performance, these schemes are only suitable to protect firmware and software patches.
- Multivariate Polynomial Cryptography: Multivariate Polynomial Cryptography: Multivariate polynomial cryptography consists of complex mathematical equations involving numerous variables. They provide compact signature generation and verification, which is advantageous in resource-limited settings such as embedded systems.
- Code-based Cryptography: Code-based cryptography research has been conducted for many decades and employs error-correcting codes for encrypting and protecting information. It provides very good security against quantum attacks and is particularly suitable for encryption applications. Although code-based cryptosystems have large public key sizes, their long history of resistance makes them a popular selection for protecting information in the long term.
How Post-Quantum Algorithms Work
A post quantum algorithm relies on the concept of using mathematical problems that are hard to break through quantum computers. They are resistant to both classical and quantum attacks. One of them, lattice-based cryptography, uses vectors in high-dimensional space. It is still very hard to solve the lattice problems even for highly powerful quantum processors.
All of the suggested algorithms test extensively for performance, key size, and resistance against any known quantum attacks. The National Institute of Standards and Technology (NIST) coordinates the worldwide effort in testing and standardizing the algorithms. They will work on new cryptographic systems used to replace current systems that are vulnerable and offer long-term security of information in a world where quantum computers are readily available and extremely powerful.
Real-World Applications of Post-Quantum Algorithms
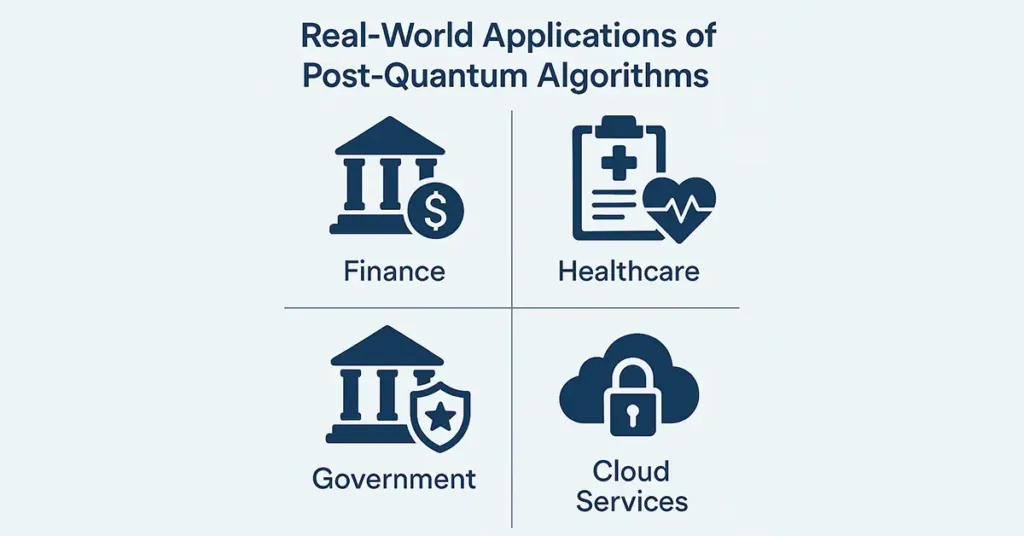
Post quantum algorithm application is not a theory. Many companies have already started using them-
- Finance: Organisations in the finance sector employ quantum-resistant cryptography to protect confidential financial transactions and customer data. Financial information is confidential for decades, and quantum-safe encryption protects it from hacking in the future. Banks and payment processors are piloting and implementing post-quantum approaches into core security solutions.
- Healthcare: The integrity and confidentiality of medical records form the basis of the healthcare business. Healthcare organizations and hospitals have been using quantum-secure encryption to secure patients’ data for decades. Health information is retained for many years, and post-quantum methods provide guarantees that such information will not be vulnerable to future computing breakthroughs.
- Government: Government departments manage national security information that may be useful for many decades. Therefore, they are leading the adoption of post-quantum technologies, primarily for secure communication and sensitive documents. Military, intelligence, and diplomatic operations are investing in quantum-resistant technologies to prepare for the future.
- Cloud Services: Cloud service providers deploy Quantum-resistant encryption. As cloud infrastructure is responsible for everything from document storage to software services, they have to ensure data protection both in transit and at rest. Cloud giants are experimenting with hybrid approaches that involve classical and post-quantum encryption to protect data even further.
Post Quantum Security in the Modern World
Security does not only mean encrypting information; it means expecting it. That is where post quantum security comes in. With billions of devices connected and more data exchanges taking place, organizations need to think ahead. One quantum attack will reveal millions of records. Adopting a post-quantum algorithm today, companies construct tomorrow-proof resilience.
Transitioning to Post Quantum Algorithms: Challenges Ahead
The transition to a post quantum algorithm presents a sequence of challenges for contemporary organizations. The majority of today’s digital architectures depend on outdated encryption algorithms such as RSA or ECC. Replacing those systems with quantum-resistant technology requires a lot of time, capital, and extensive testing. Post-quantum techniques have greater key lengths and increased computational overhead, affecting performance, particularly on outdated hardware.
To control this transition, companies have to start with proper risk analysis. Companies have to tag the systems handling sensitive or long-term data and have them upgraded initially. Having a clear migration timeline guarantees the process will be seamless. With early execution and adopting hybrid cryptography, companies can phase their systems gradually while being in advance of the quantum attack without sacrificing the security level.
Governments and Global Efforts Toward Quantum Safety
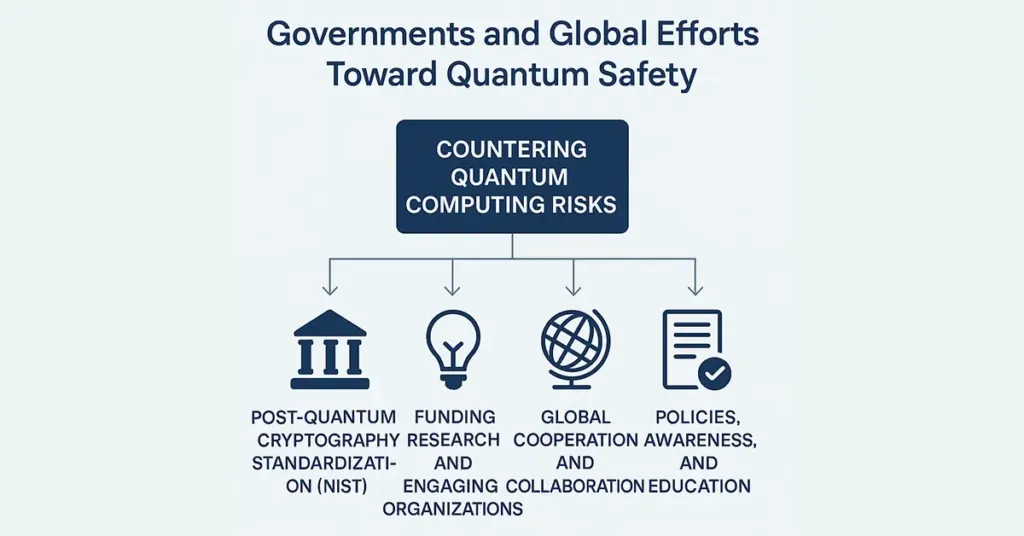
Governments across the globe are actively engaging in countering quantum computing risks. Governments recognize that tomorrow’s encryption must be quantum-resistant. Organizations such as the National Institute of Standards and Technology (NIST) spearhead initiatives globally by conducting the Post-Quantum Cryptography Standardization Process. The process is to identify the best post quantum algorithm to implement worldwide.
Parallely, nations finance research, sponsor academic research, and engage with private technology companies to develop quantum-resistant digital infrastructures. For the effectiveness of these breakthroughs, global cooperation is necessary. Governments need to collaborate in developing transparent policies, raising awareness, and providing education on quantum-safe procedures. These steps will determine the future of secure communications and data protection.
Understanding Post Quantum Encryption Technologies
Post quantum encryption employs post-quantum-resistant methods to encrypt digital information. This is in conjunction with a post quantum algorithm, which protects encrypted information such that no individual, even quantum computers, can access it. Whether it is emails, financial data, or government documents being protected, encryption is an essential aspect of data protection. Companies embracing quantum encryption today will be tomorrow’s leaders.
The Evolution of Cryptography with Post Quantum Cryptography
Post quantum cryptography is the future of secure communication. Traditional cryptographic systems based on problems like factorization are no longer efficient. Post quantum algorithms are not based on the same methods as traditional algorithms and quantum computers cannot easily solve them. This new area of cryptography ensures that when our computers get faster, our encryption doesn’t get weaker.
The Role of Blockchain and Post Quantum Blockchain Innovation
Blockchain relies on trust and cryptography. Quantum computing imperils that trust. Post quantum blockchain incorporates post-quantum algorithms as an integral part of its design. This safeguards smart contracts, transactions, and digital identity. Quantum-resistant blockchain may be the future of safe digital transactions in a post-quantum economy.
Emerging Standards and Post Quantum Secure Blockchain
Post quantum secure blockchain marries blockchain’s openness with post-quantum algorithmic security. They will be the foundation of future technologies—supply chains, digital identity, and a lot more. They will be safeguarded with the security, post-quantum proven algorithms, to provide the highest level of security and endurance.
Conclusion
The advent of quantum computing demands a complete rethinking of computer security. Old-school encryption won’t survive the transition. It’s because of this that the post-quantum algorithm isn’t simply an improvement—it’s necessary.
With global effort, new standards, and industry-wide consciousness, the transition has already begun. By adopting post-quantum algorithms, we anticipate our systems, data, and digital life for the inevitable. The quantum future arrives, but armed with the right tools, our encryption will last.
FAQs
What is a post quantum algorithm?
A post quantum algorithm is a cryptography algorithm resistant against attacks by a quantum computer. Unlike regular encryption based on the difficulty of factoring numbers or discrete logarithms, a post quantum algorithm makes use of more complex problems hard for a quantum computer but simple for a classical computer. These are lattice-based, multivariate, or hash-based constructions.
Why are post quantum algorithms important?
These algorithms are vital to long-term data protection. Existing cryptographic techniques, such as RSA and ECC, will be made obsolete when quantum computers advance. Quantum computers are capable of breaking their underlying issues within seconds. A post quantum algorithm, however, is designed to hold up to these kinds of attacks.
Are there post quantum algorithms available today?
Yes, certain industries have begun implementing them. The banking sector, military departments, and certain high-technology corporations are experimenting with them on closed networks. They are being implemented on pilot applications, test environments, and hybrid cryptographic schemes. Not yet fully standardized themselves, post quantum algorithm implementations’ early deployment does provide an opportunity to experiment with their usability and efficacy in field conditions.
What are the differences between post quantum algorithms and classical ones?
Classic algorithms such as RSA and ECC are based on mathematical issues that can be easily solved by quantum computers using algorithms such as Shor’s. A post quantum algorithm is free from such vulnerabilities. It is based on completely different mathematical principles. For example, lattice-based cryptography resists quantum attacks and operates differently compared to number-based techniques. This makes them significantly more resilient in a quantum computer world.
Who is working on post quantum algorithms?
The onus is on technology firms, national laboratories, and research institutes. The National Institute of Standards and Technology (NIST) takes the lead. Cryptographers, cybersecurity organizations, and universities all around the world are also a part of it. They all test, verify, and innovate each post quantum algorithm submitted to them. The partnering is towards its global use and legitimacy.
Do quantum computers currently break encryption?
Not yet. Current quantum computers are not yet substantial enough to crack secure encryption such as RSA-2048. But all experts agree they will be someday. That looming threat necessitates an early move to post quantum algorithm strategies. Information that is safe today can be at risk tomorrow, particularly if it is intercepted and saved for later decryption.
Which industries are most benefited by post quantum algorithms?
Applications holding long-term, sensitive data are most benefited. Banks have to secure transactions. Medical providers have to keep patient data secure. Military networks depend on secure communication. Cloud services that hold massive repositories of personal data also require additional protection.
What is the role of NIST in post quantum algorithm development?
NIST is in charge of standardization. NIST initiated an international competition to determine the top post quantum algorithm candidates. NIST evaluated submissions over a few years, tested them under stress, and considered their alternatives. Its final choices will be world standards that will be followed by organizations everywhere.
What secures future information with a post quantum algorithm?
Even if data is intercepted today in an encrypted state, a post quantum algorithm ensures that it will not be able to decrypt it tomorrow. Because mathematics used in it is secure against both classical as well as quantum attacks. That ensures your data to be private not only for months but decades.
Are post quantum algorithms mature enough for large-scale deployment?
A few of them are nearing completion. After NIST completes its review, governments, firms, and cloud infrastructures will begin full-scale adoption. In the meantime, the majority are opting for hybrid models, merging traditional and post quantum algorithm systems as an added layer of security.
References-
(Chad Boutin, NIST Announces First Four Quantum-Resistant Cryptographic Algorithms)
(Dylan Rudy, Post-Quantum Cryptography, Explained)
